How to Use a Single IAM User to Easily Access All Your Accounts by Using the AWS CLI | AWS Security Blog
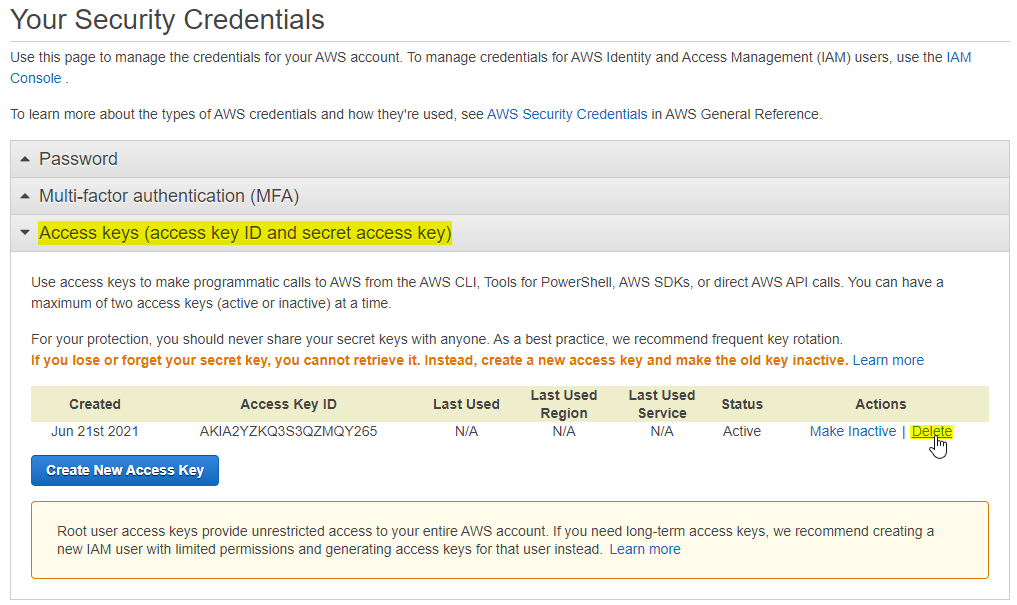
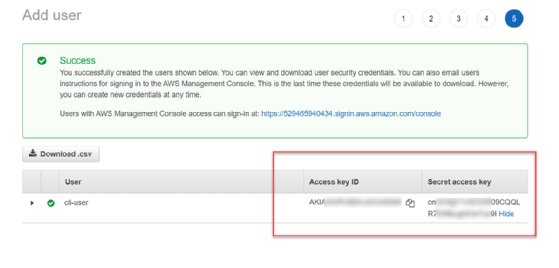
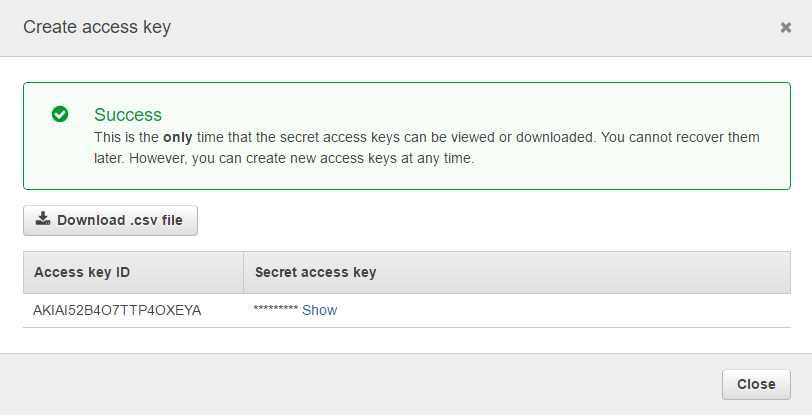
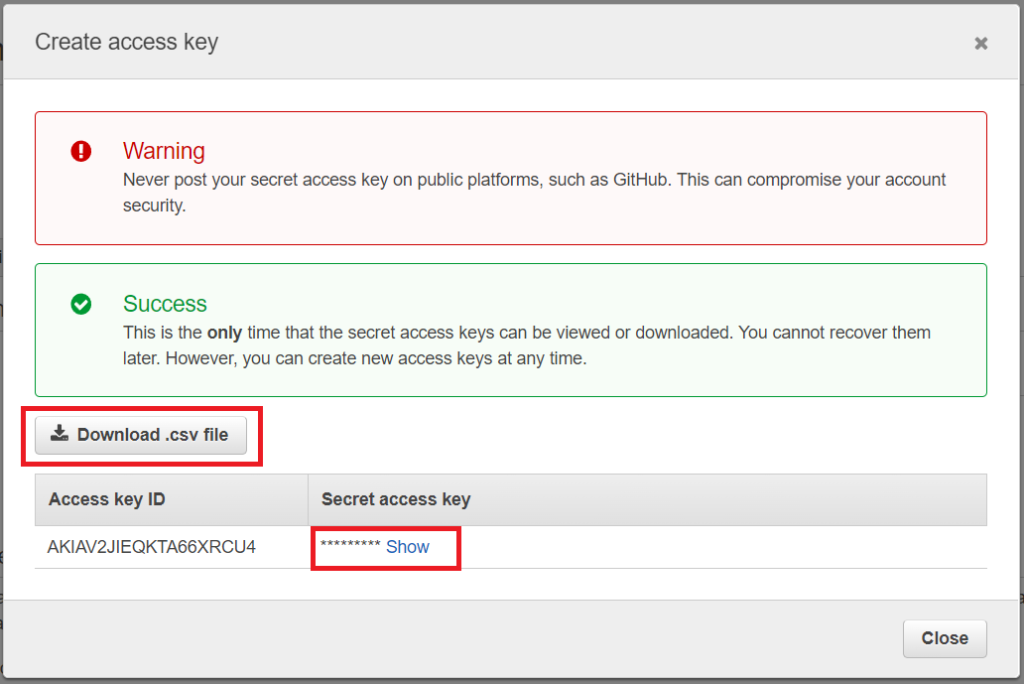
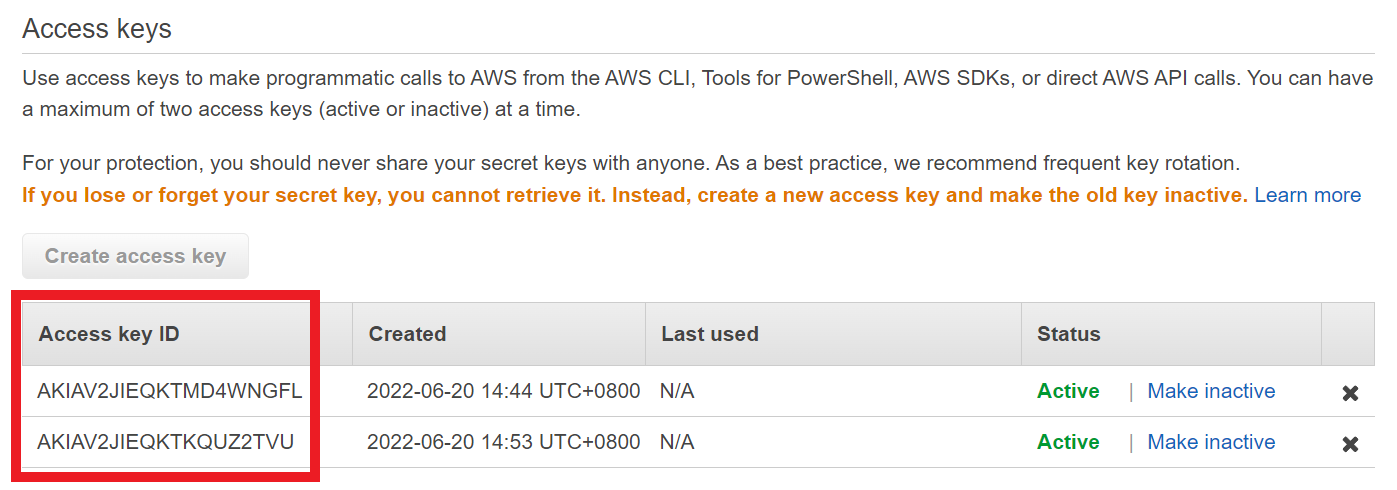
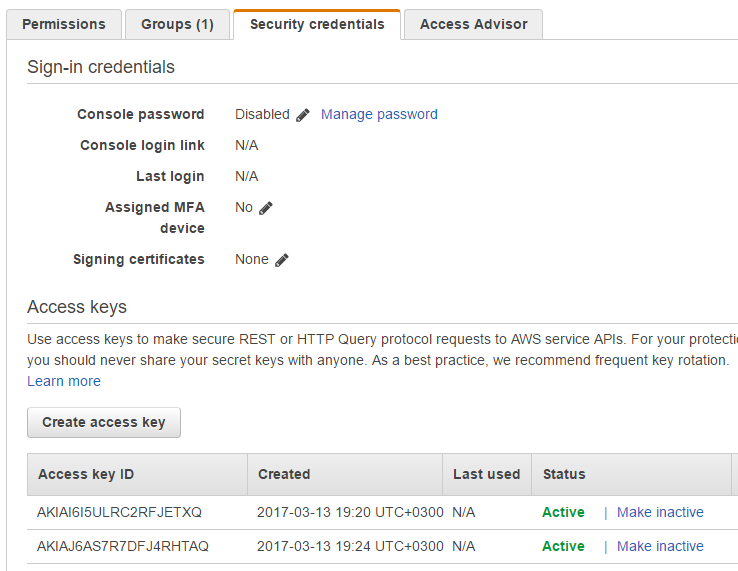
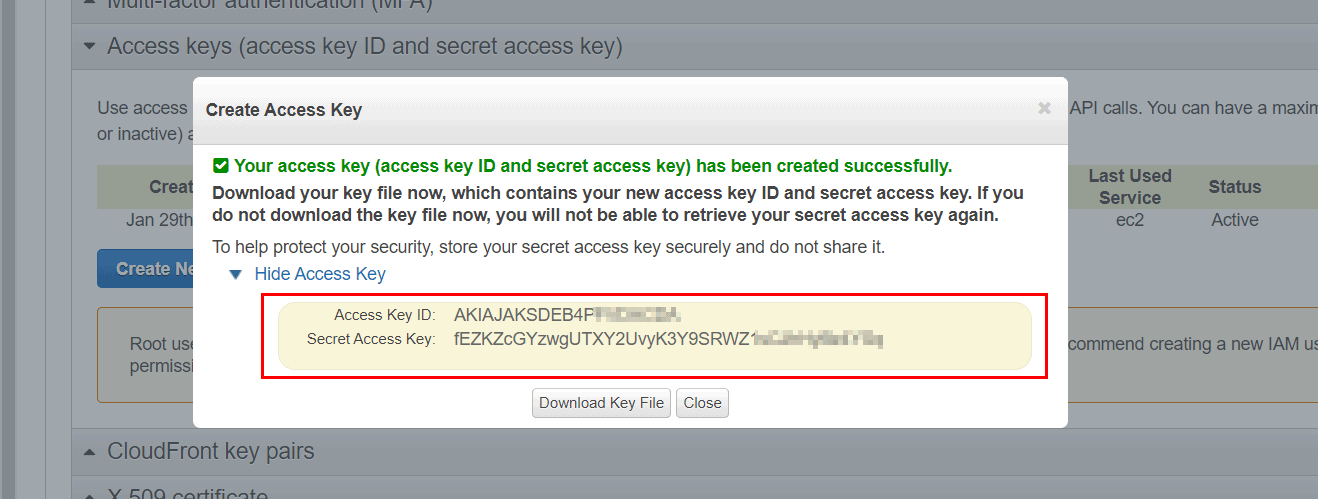
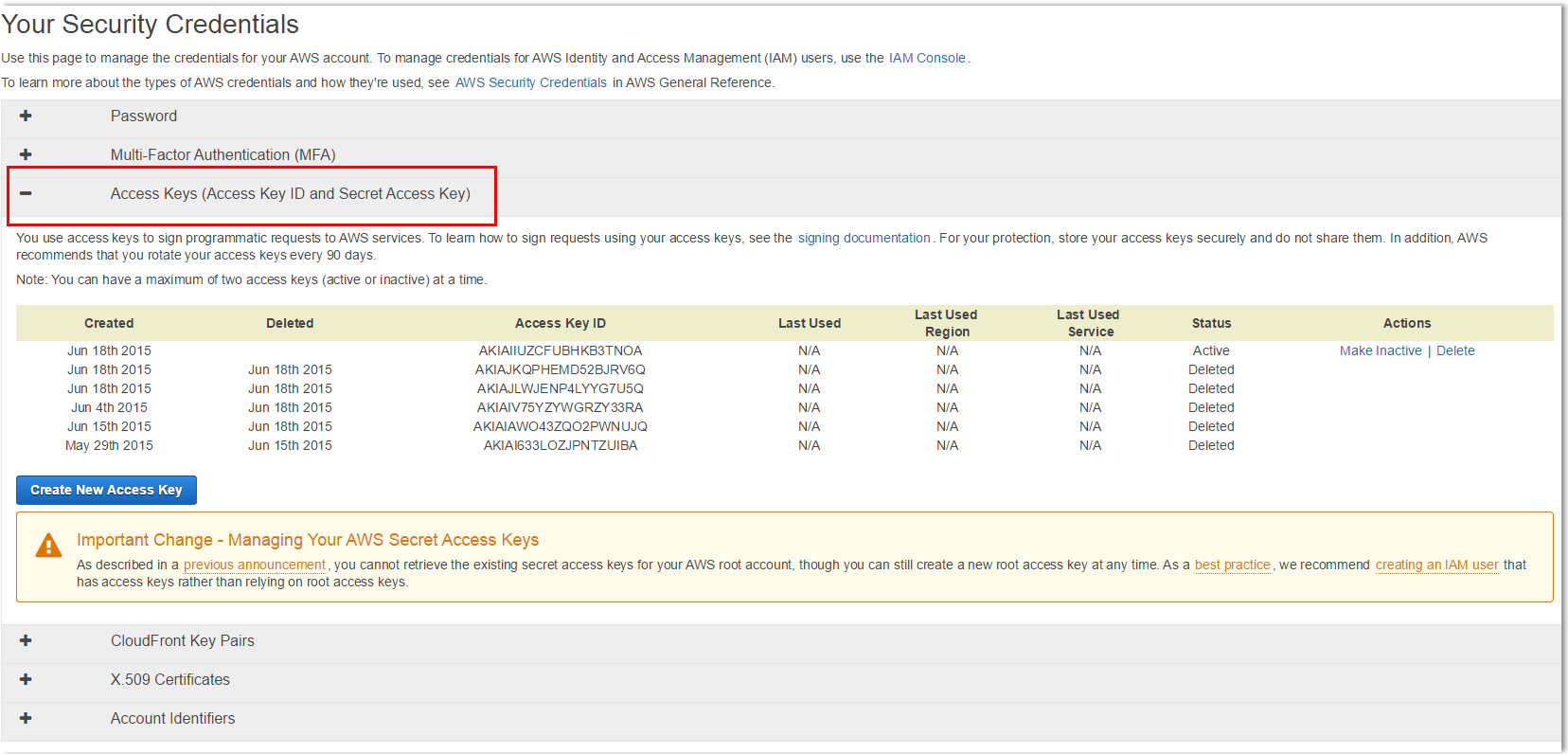
Access Key Id and Secret Access Key. How to retrieve your AWS Access Keys and use them to access Amazon S3.
Access Key Id and Secret Access Key. How to retrieve your AWS Access Keys and use them to access Amazon S3.
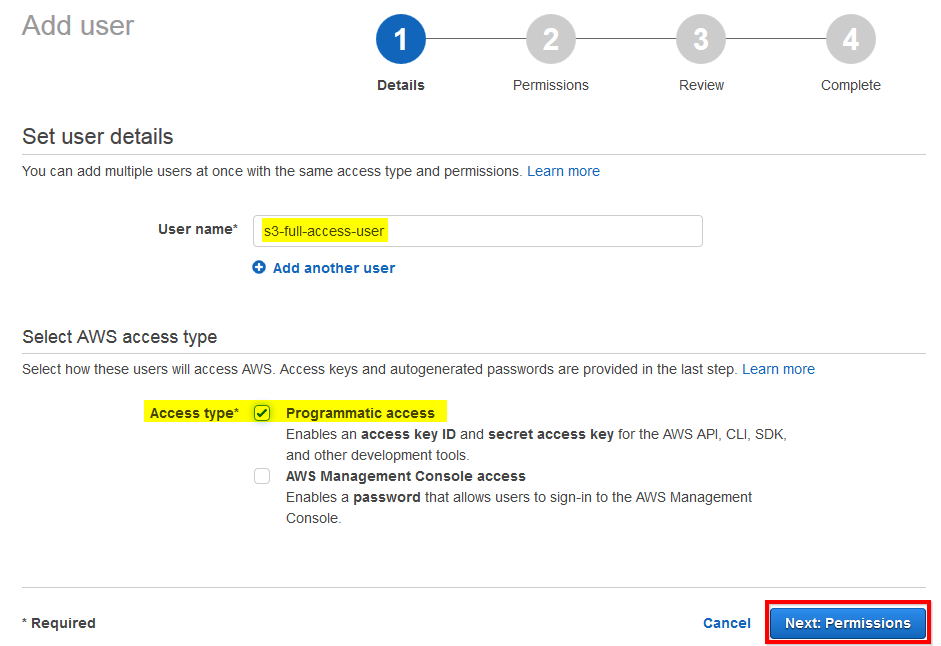
AWS Access Keys - Access Key Id and Secret Access Key. Where to obtain Access Keys and how to use them to connect Amazon S3.
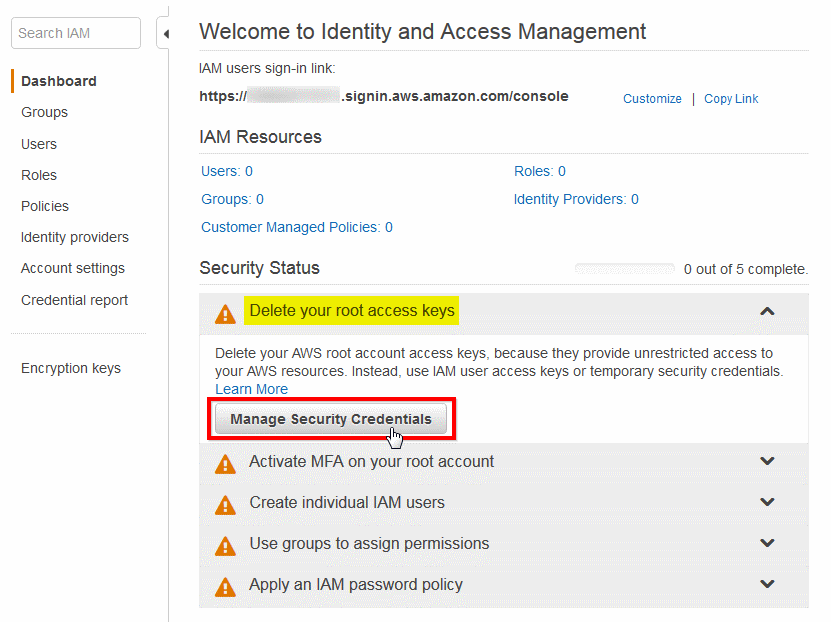
AWS Access Keys - Access Key Id and Secret Access Key. Where to obtain Access Keys and how to use them to connect Amazon S3.