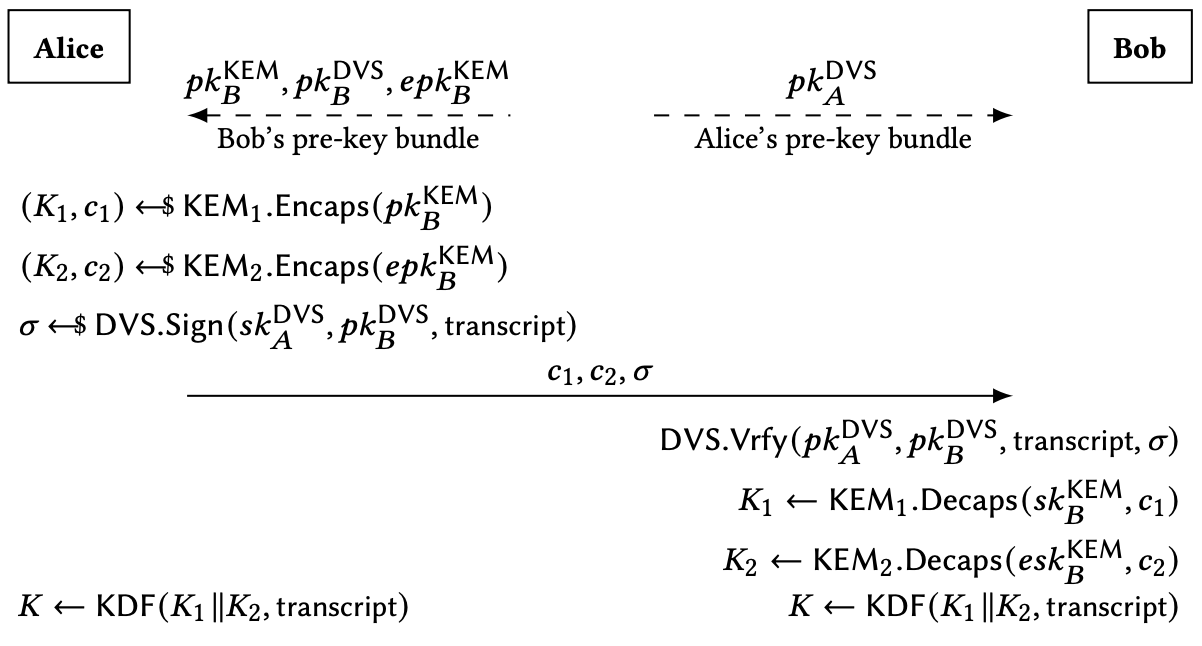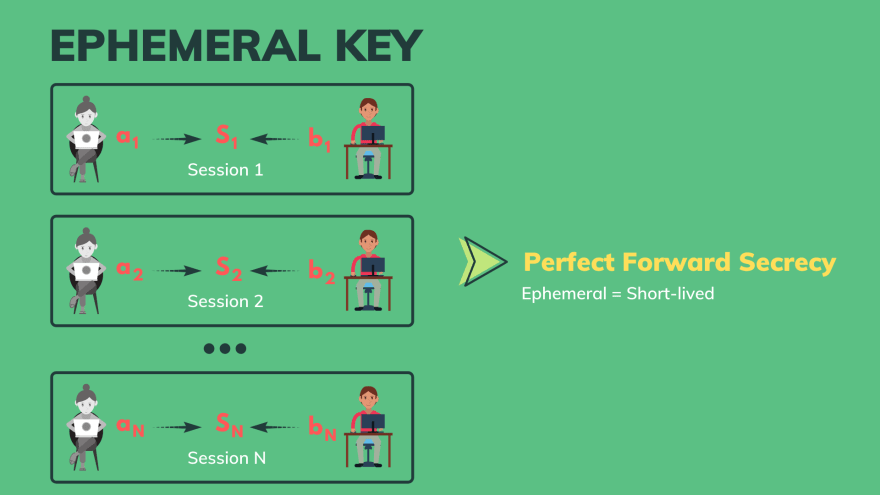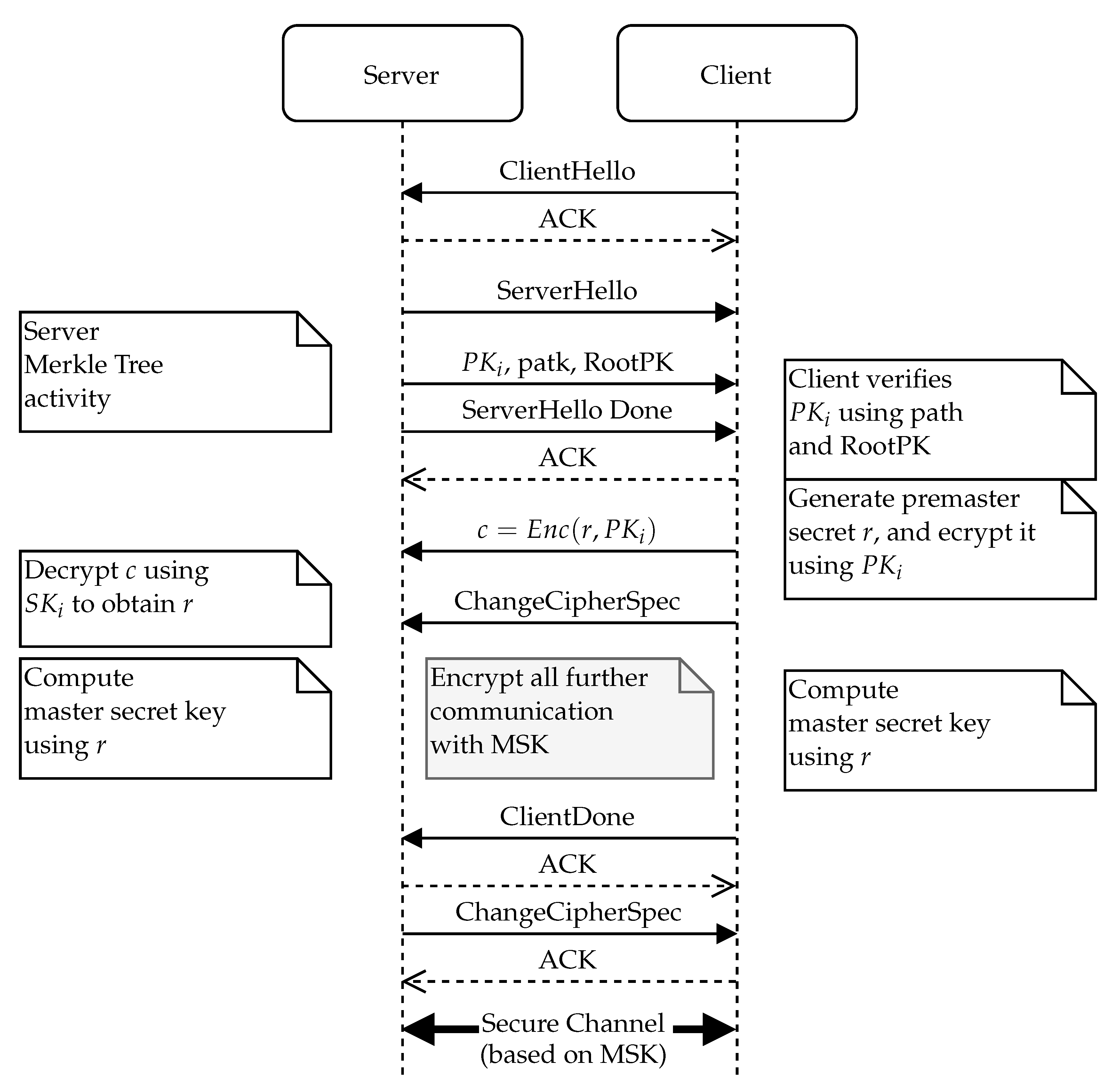
Sensors | Free Full-Text | Ephemeral Keys Authenticated with Merkle Trees and Their Use in IoT Applications
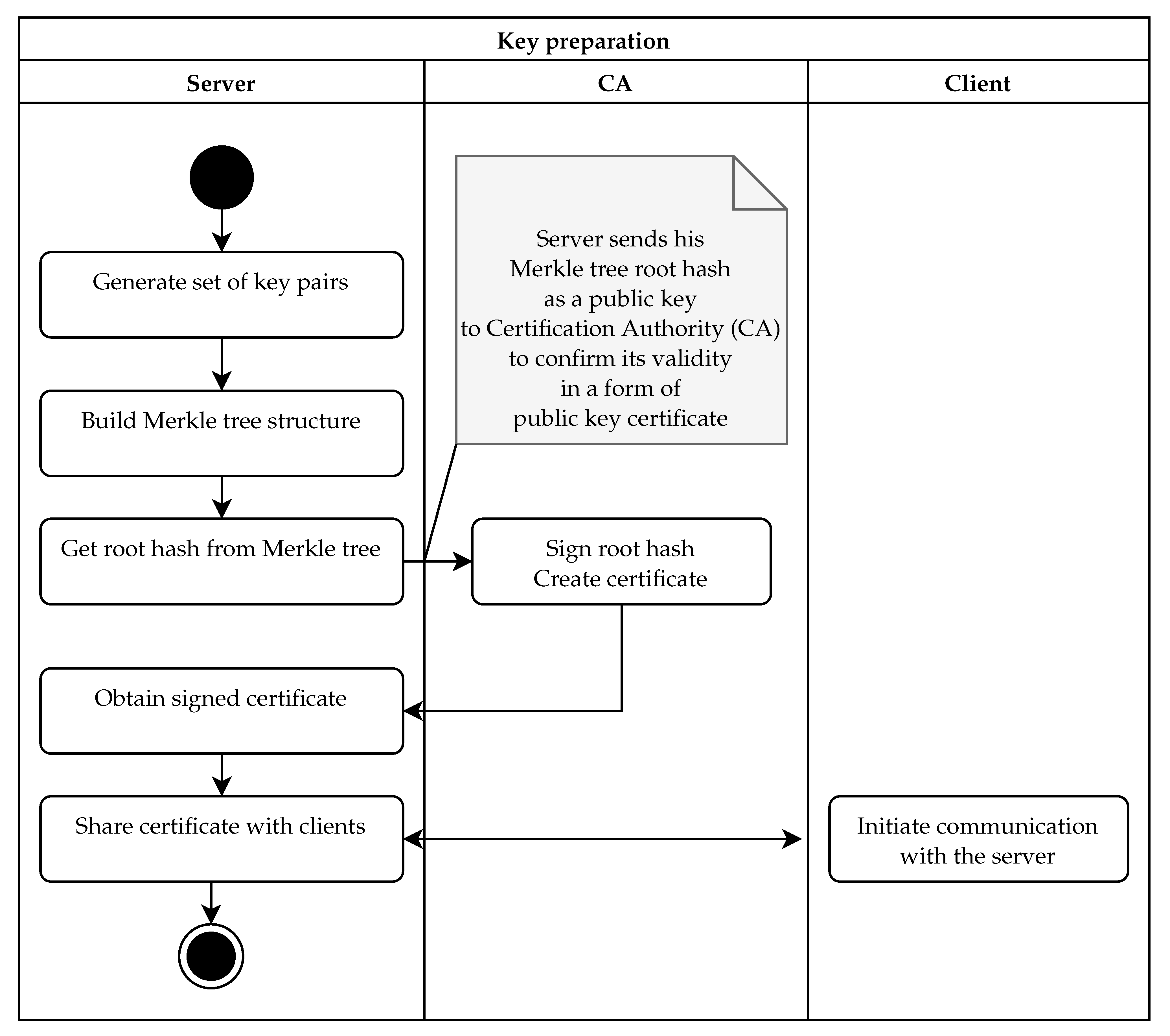
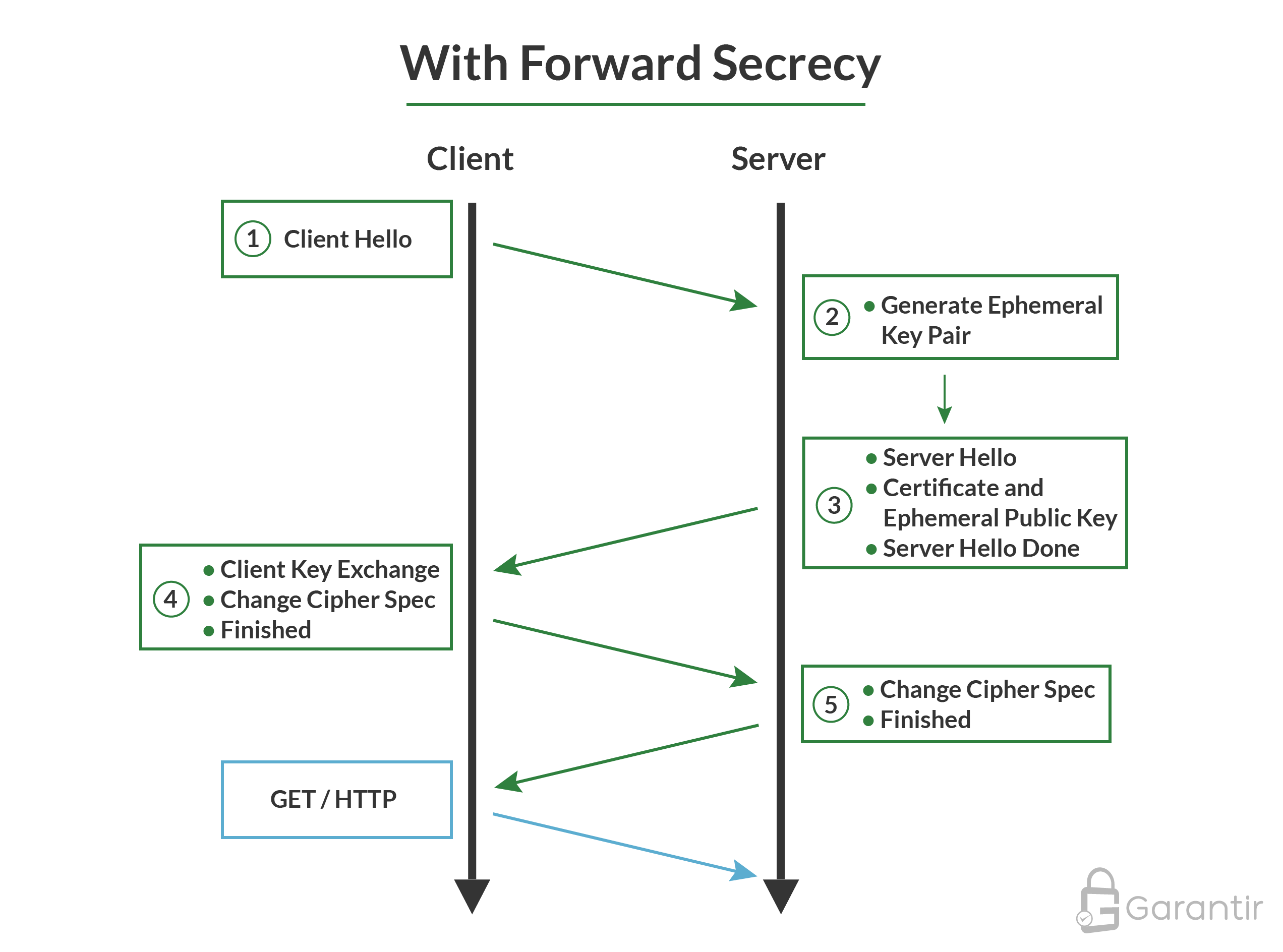
Sensors | Free Full-Text | Ephemeral Keys Authenticated with Merkle Trees and Their Use in IoT Applications
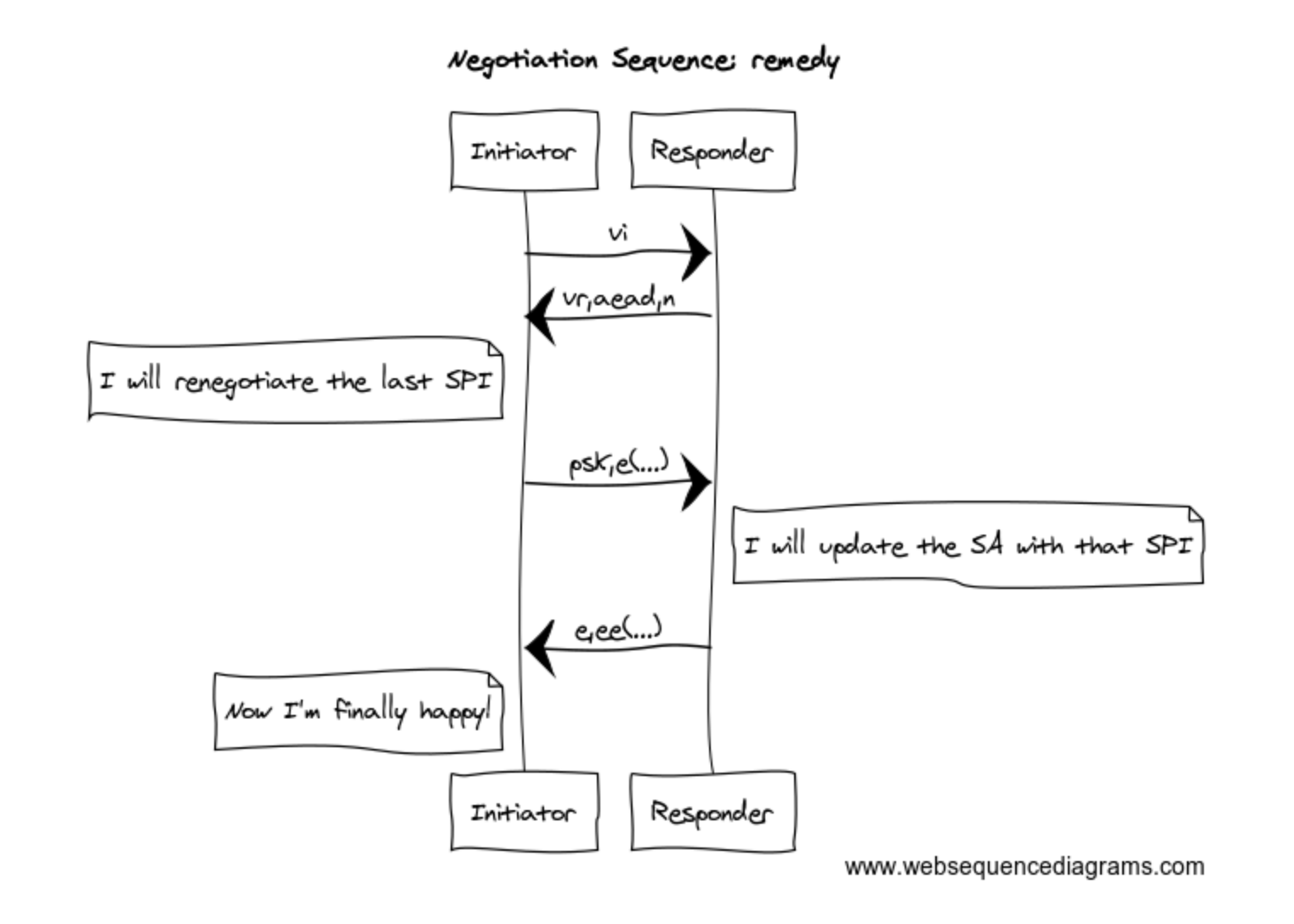
FR: Give Control over Ephemeral Key Instance Removal Duration · Issue #4798 · tailscale/tailscale · GitHub
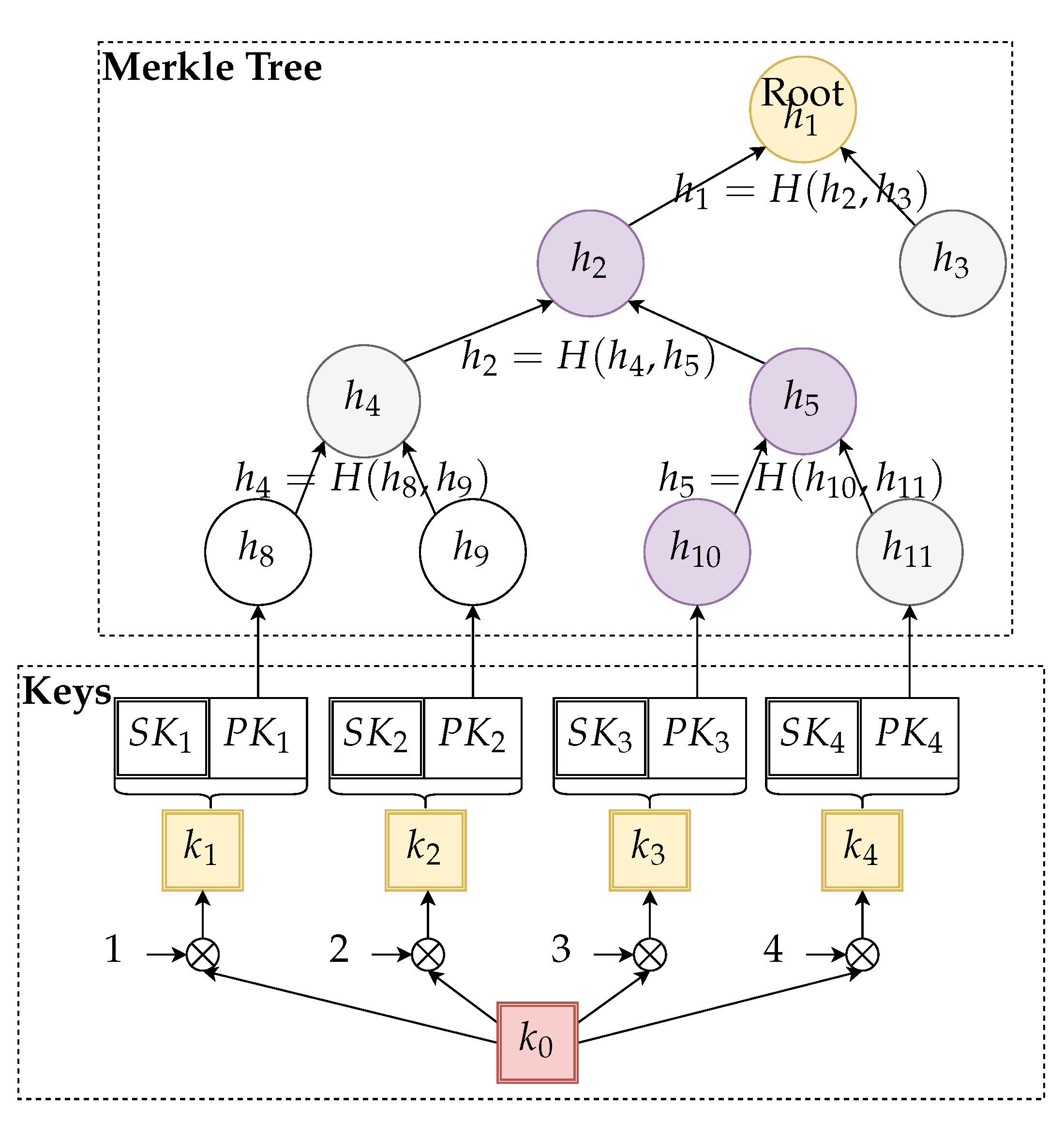
Sensors | Free Full-Text | Ephemeral Keys Authenticated with Merkle Trees and Their Use in IoT Applications