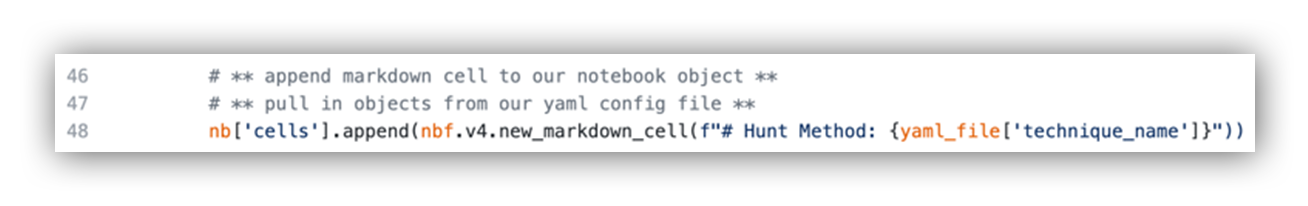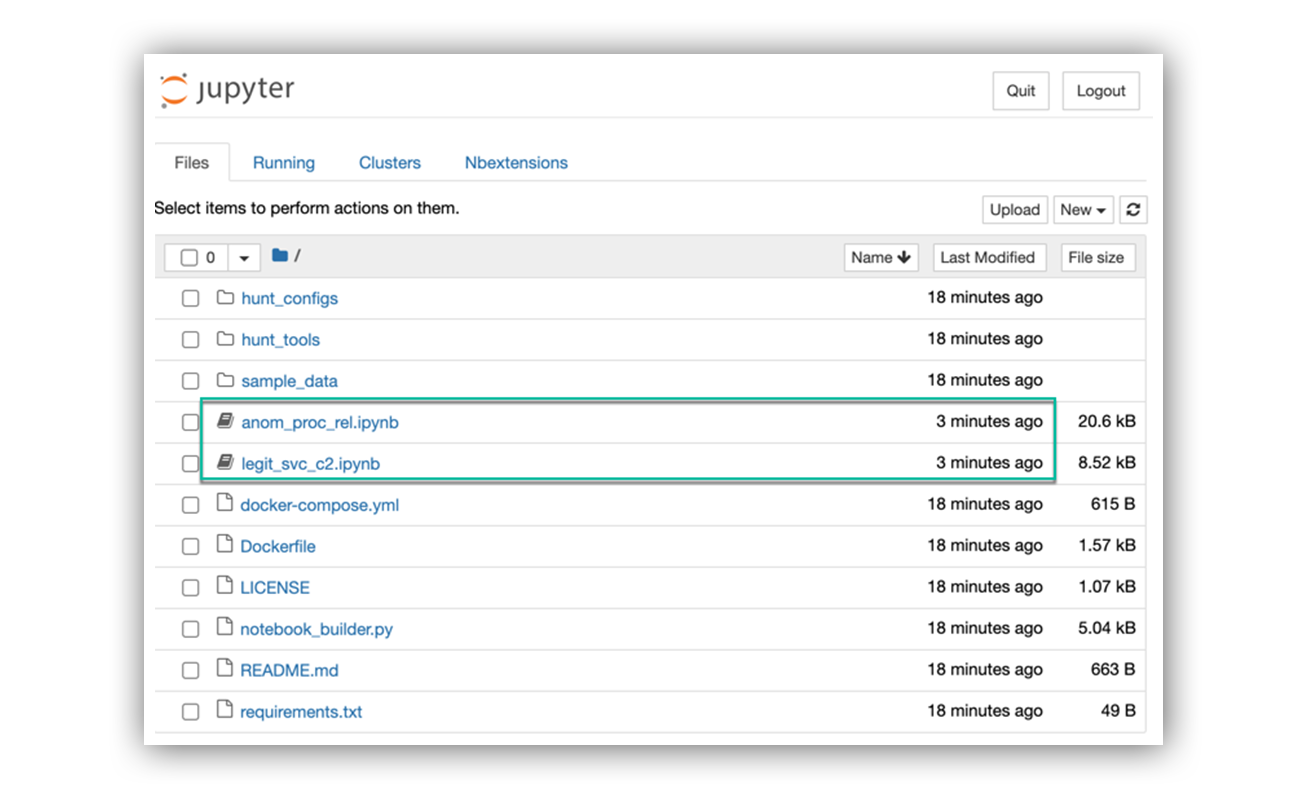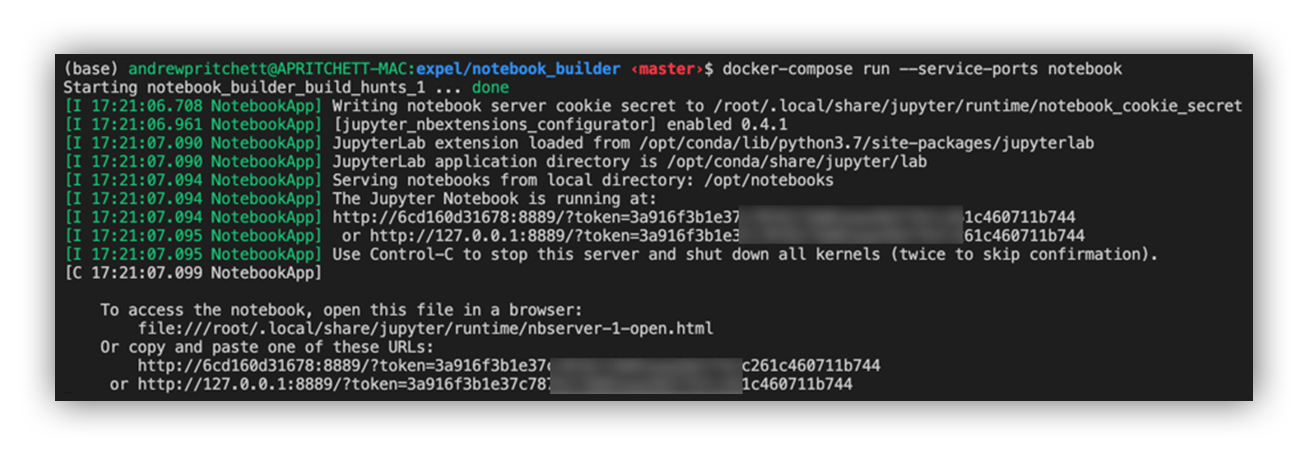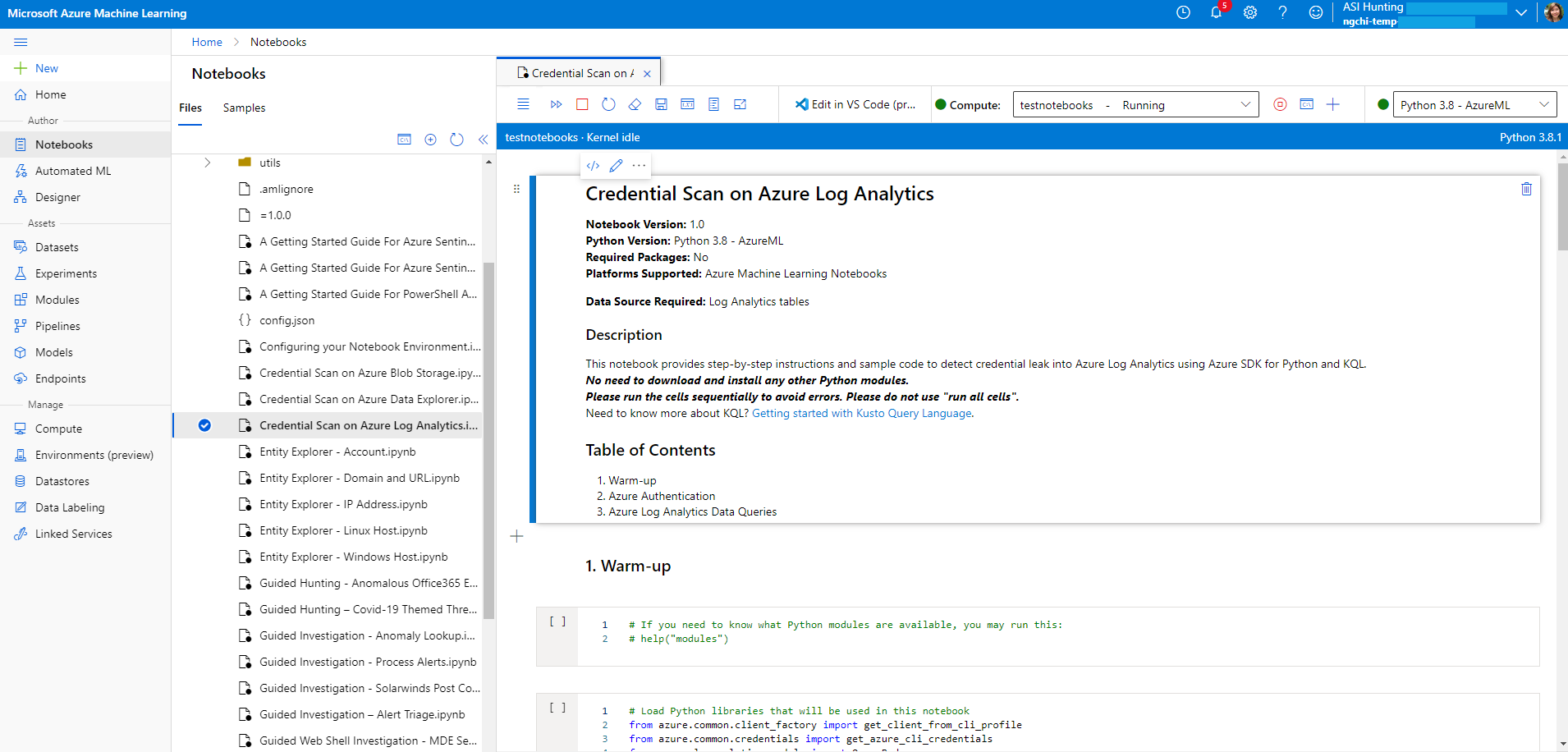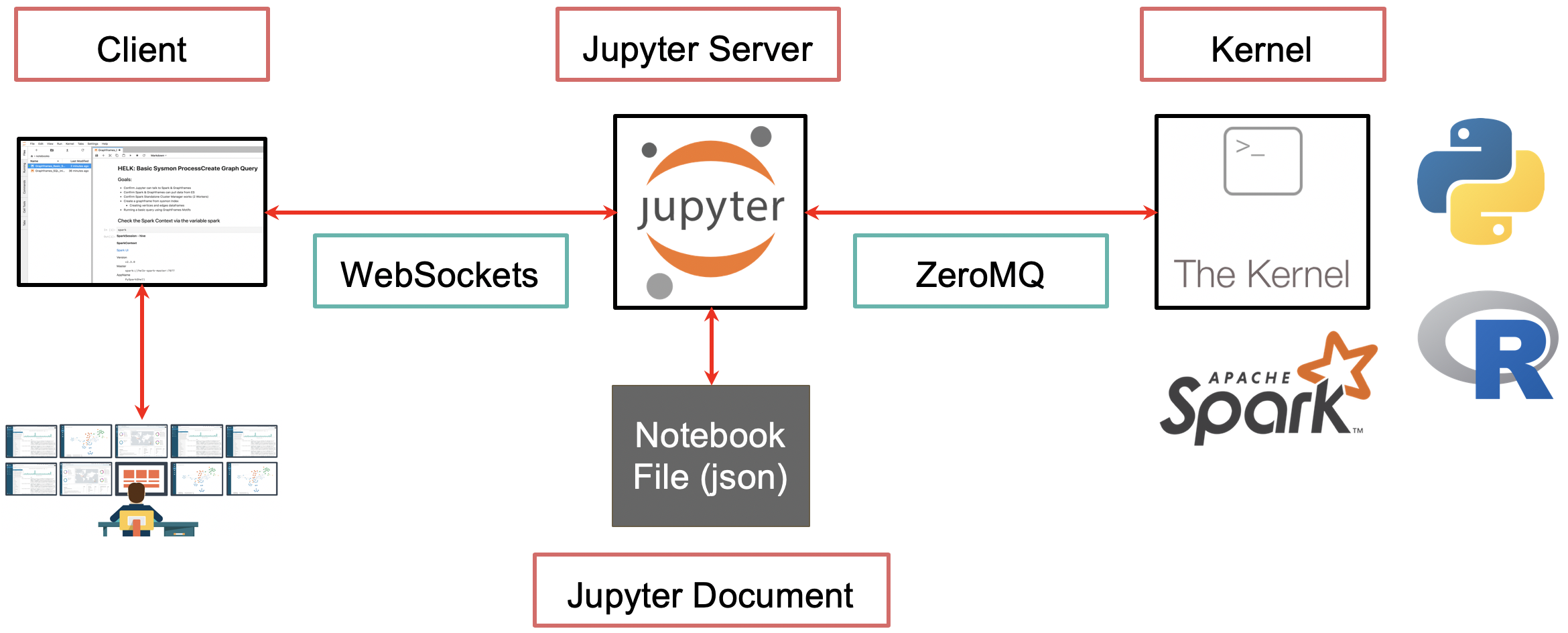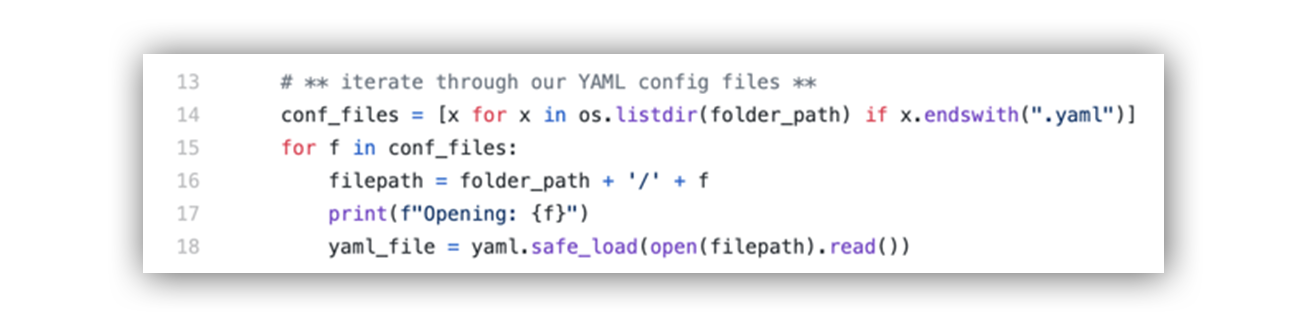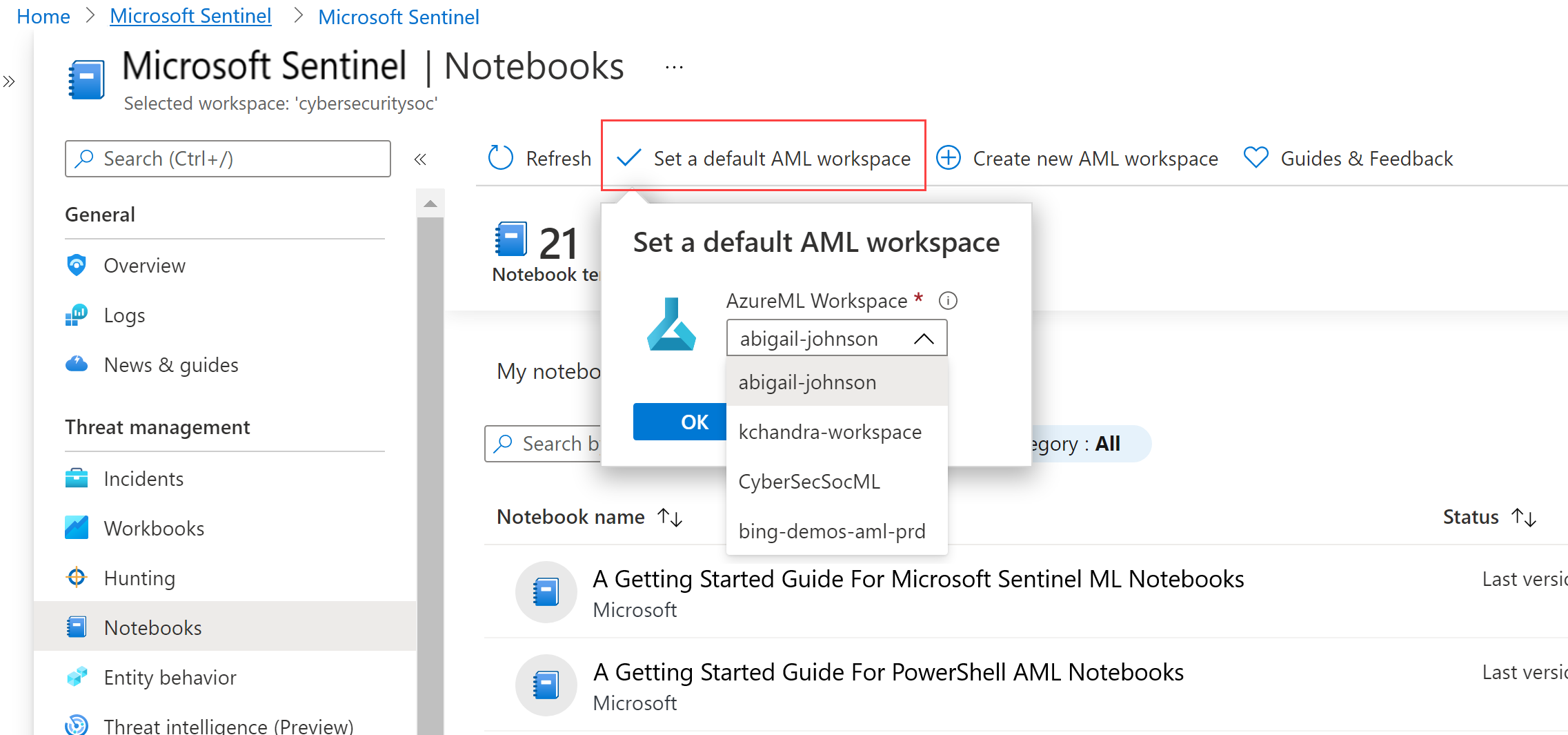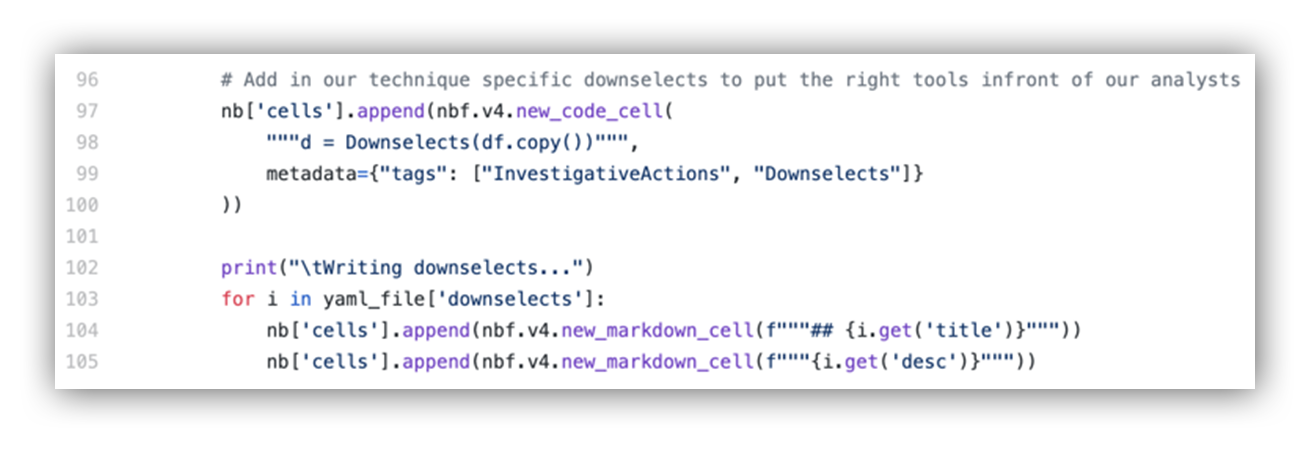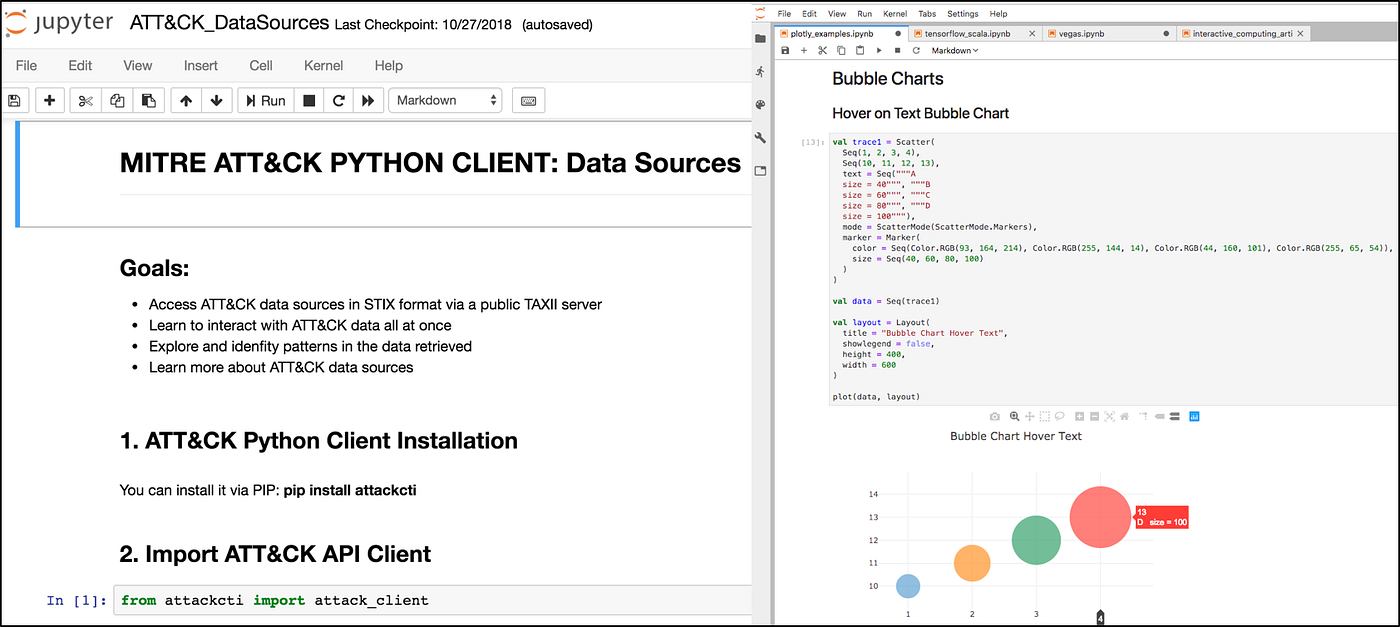
Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓 | by Roberto Rodriguez | Posts By SpecterOps Team Members
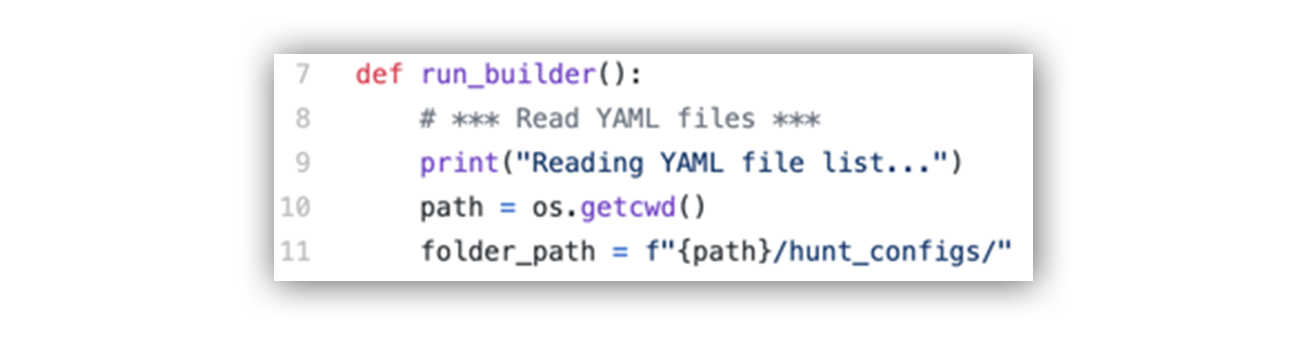
GitHub - ThreatHuntingProject/hunter: A threat hunting / data analysis environment based on Python, Pandas, PySpark and Jupyter Notebook.

Writing an Interactive Book 📖 over the Threat Hunter Playbook 🏹 with the help of the Jupyter Book Project 💥 | by Roberto Rodriguez | Open Threat Research | Medium
Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓 | by Roberto Rodriguez | Posts By SpecterOps Team Members

Writing an Interactive Book 📖 over the Threat Hunter Playbook 🏹 with the help of the Jupyter Book Project 💥 | by Roberto Rodriguez | Open Threat Research | Medium

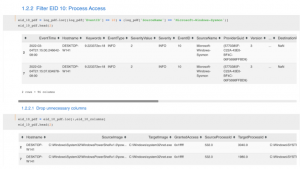
Threat Hunting Series : Using Jupyter Notebook Analyzing Excessive Usage of FTP User Scenario | by Rifqi Ardia Ramadhan | MII Cyber Security Consulting Services | Medium

Threat Hunting with Jupyter Notebooks— Part 1: Your First Notebook 📓 | by Roberto Rodriguez | Posts By SpecterOps Team Members