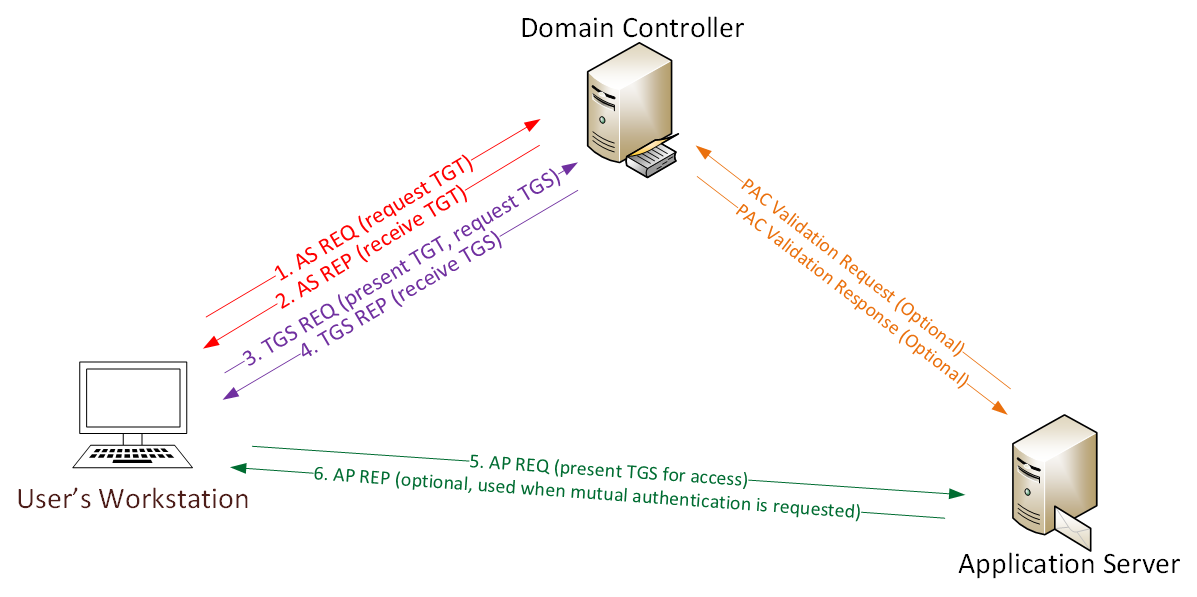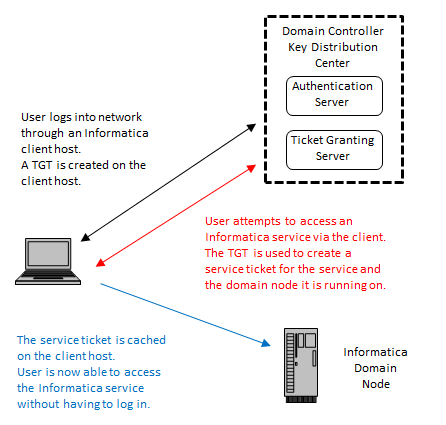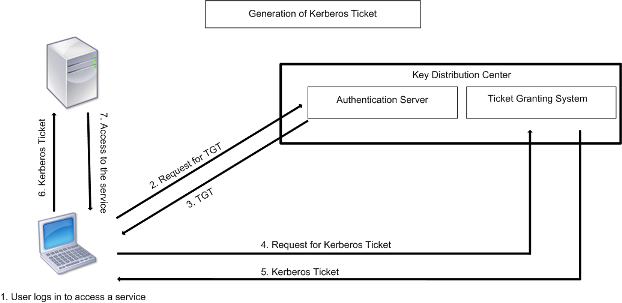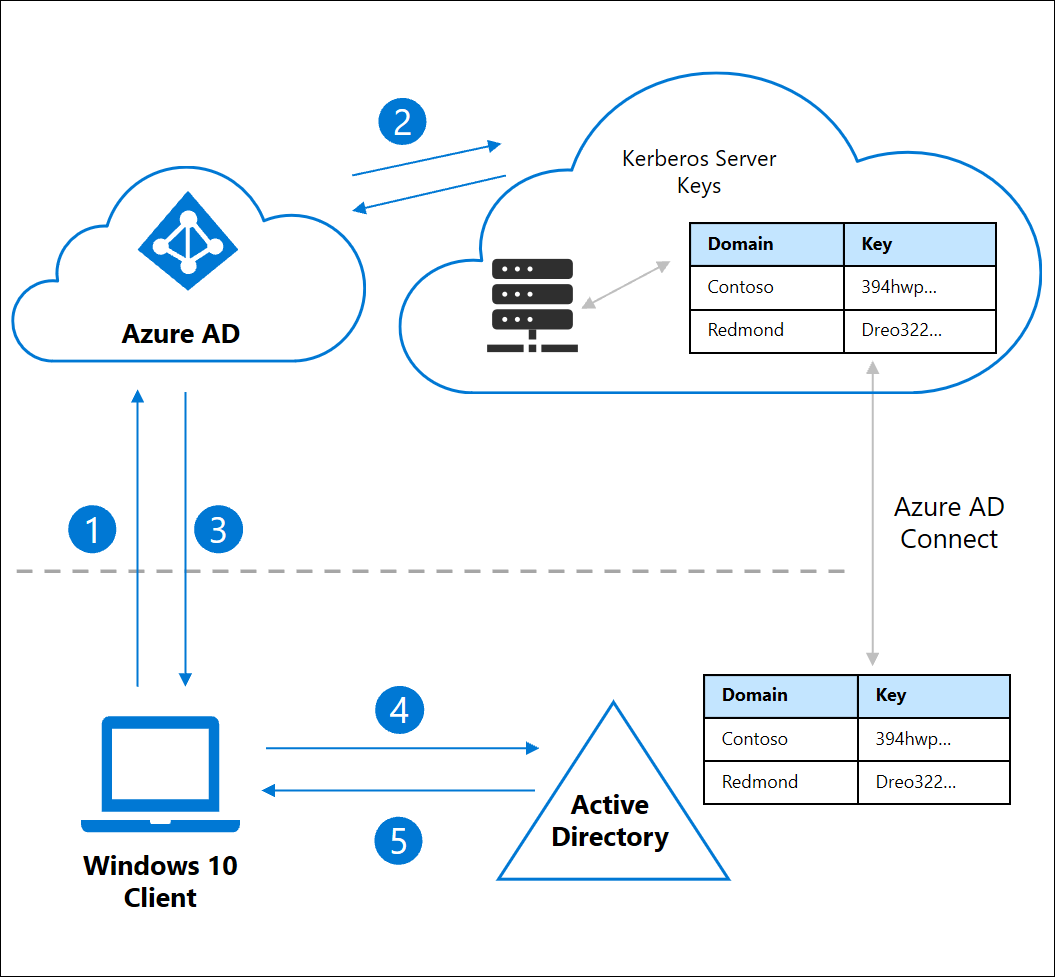
Kennwortlose Anmeldung mit Sicherheitsschlüsseln bei lokalen Ressourcen – Azure Active Directory - Microsoft Entra | Microsoft Learn

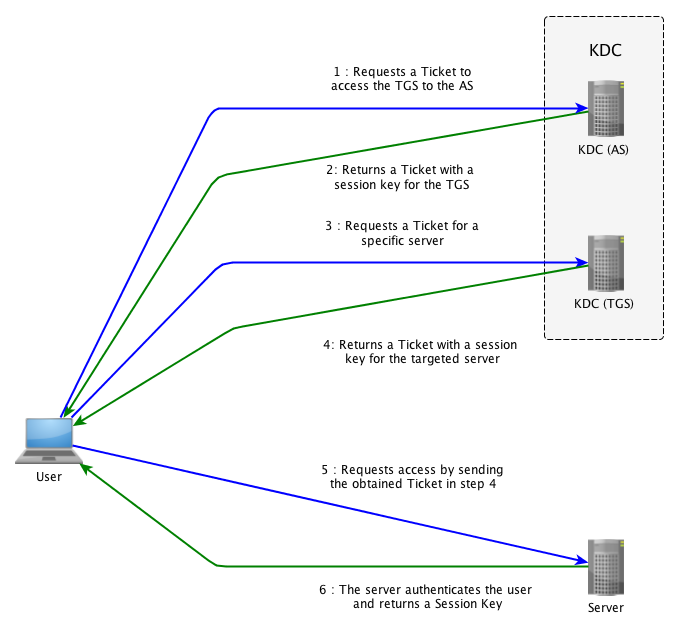
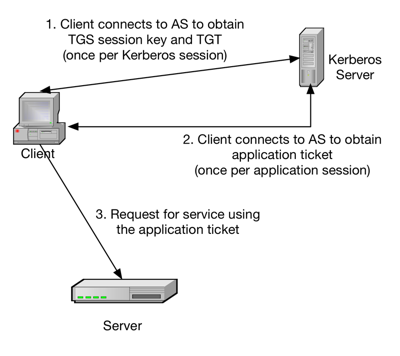
1 A simplified version of the Kerberos authentication system: both the... | Download Scientific Diagram
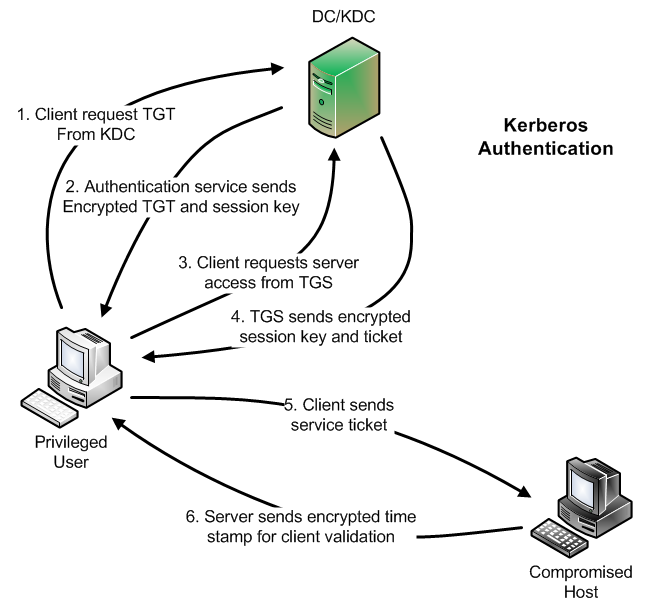
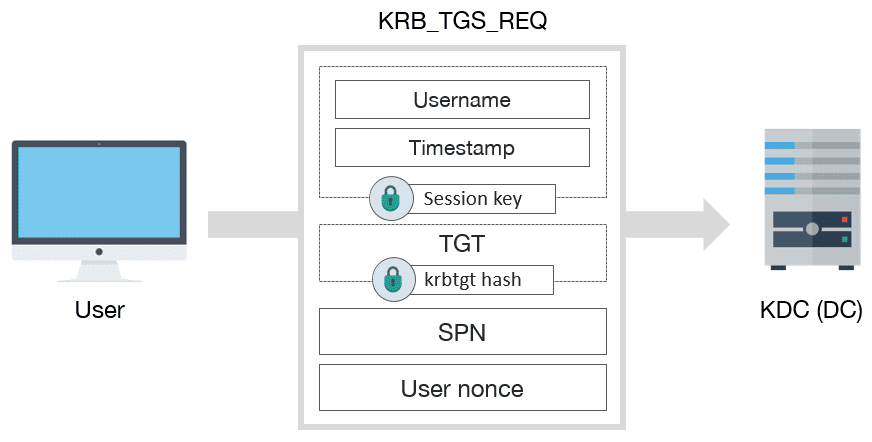
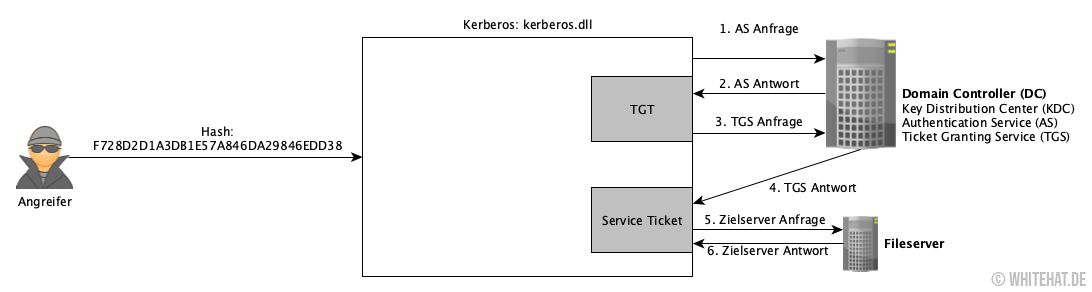
SANS Digital Forensics and Incident Response Blog | Kerberos in the Crosshairs: Golden Tickets, Silver Tickets, MITM, and More | SANS Institute
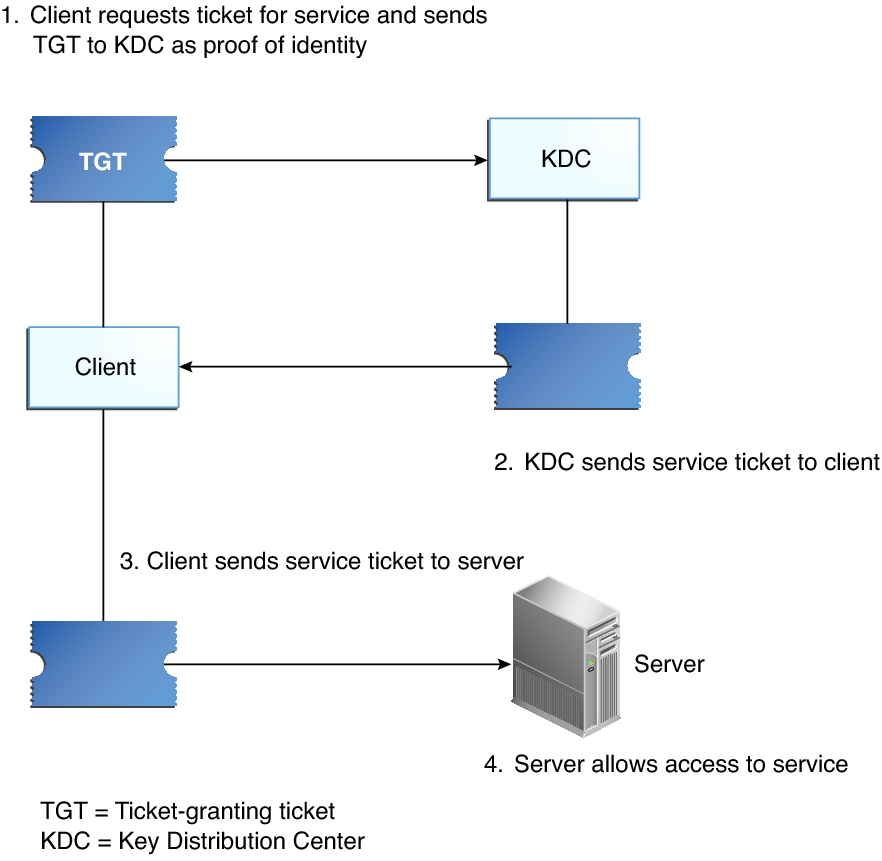
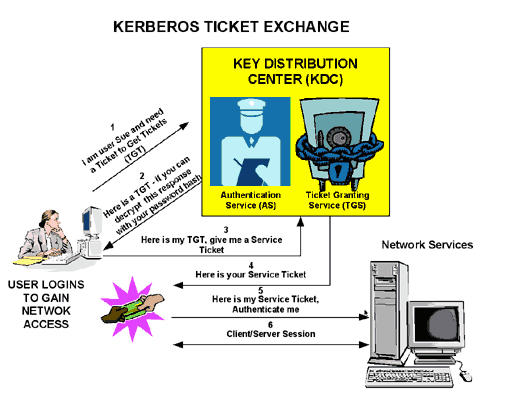
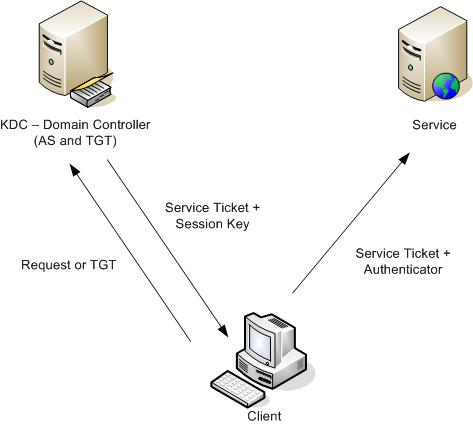
How the Kerberos Service Works - Managing Kerberos and Other Authentication Services in Oracle® Solaris 11.3