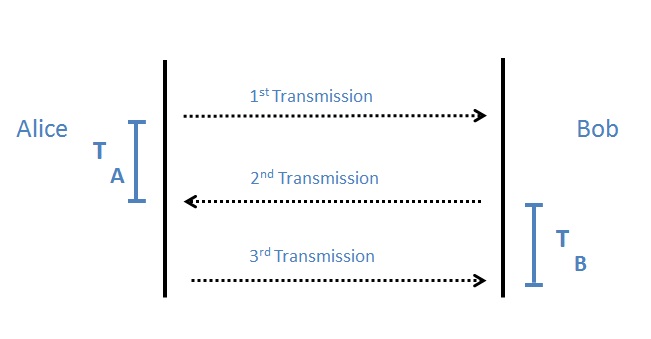
![PDF] An improved conference-key agreement protocol for dynamic groups with efficient fault correction by Orhan Ermis, Şerif Bahtityar, Emin Anarim, M. Ufuk Caglayan · 10.1002/sec.1089 · OA.mg PDF] An improved conference-key agreement protocol for dynamic groups with efficient fault correction by Orhan Ermis, Şerif Bahtityar, Emin Anarim, M. Ufuk Caglayan · 10.1002/sec.1089 · OA.mg](https://og.oa.mg/An%20improved%20conference-key%20agreement%20protocol%20for%20dynamic%20groups%20with%20efficient%20fault%20correction.png?author=%20Orhan%20Ermis,%20%C5%9Eerif%20Bahtityar,%20Emin%20Anarim,%20M.%20Ufuk%20Caglayan)
PDF] An improved conference-key agreement protocol for dynamic groups with efficient fault correction by Orhan Ermis, Şerif Bahtityar, Emin Anarim, M. Ufuk Caglayan · 10.1002/sec.1089 · OA.mg
GitHub - jcmorais/Diffie-Hellman-key-agreement-protocol: Implementation explicit of the Diffie-Hellman key agreement protocol in Java

An efficient and secure Diffie–Hellman key agreement protocol based on Chebyshev chaotic map - ScienceDirect

Authentication and Key Agreement Protocols: Cryptanlysis and Design : Mangipudi, Kumar: Amazon.de: Bücher

PPT - Elliptic Curve Authenticated Key Agreement Protocol (ECAKA) PowerPoint Presentation - ID:4546393
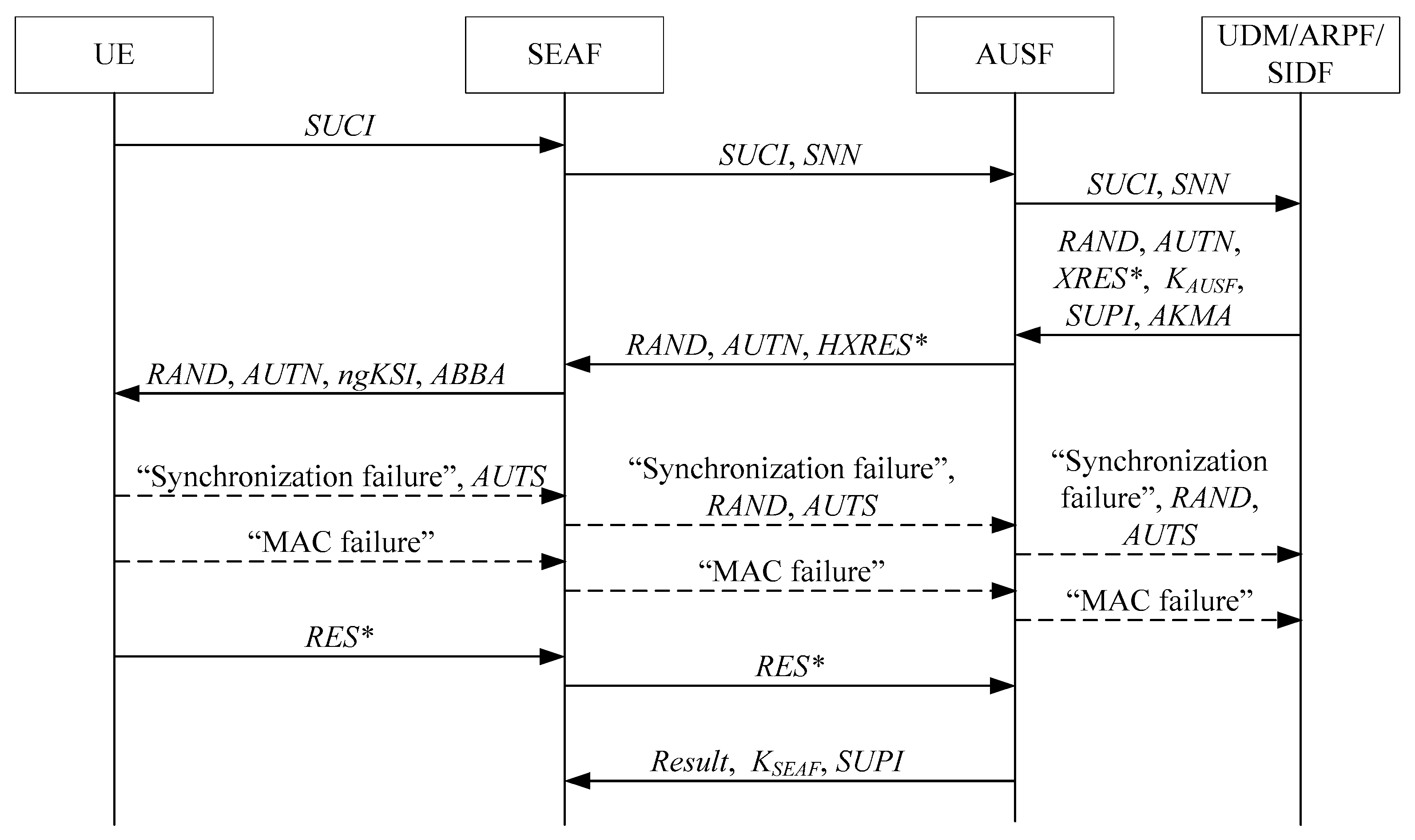
Information | Free Full-Text | 5GAKA-LCCO: A Secure 5G Authentication and Key Agreement Protocol with Less Communication and Computation Overhead
An Enhanced Biometric Based Authentication with Key-Agreement Protocol for Multi-Server Architecture Based on Elliptic Curve Cryptography | PLOS ONE
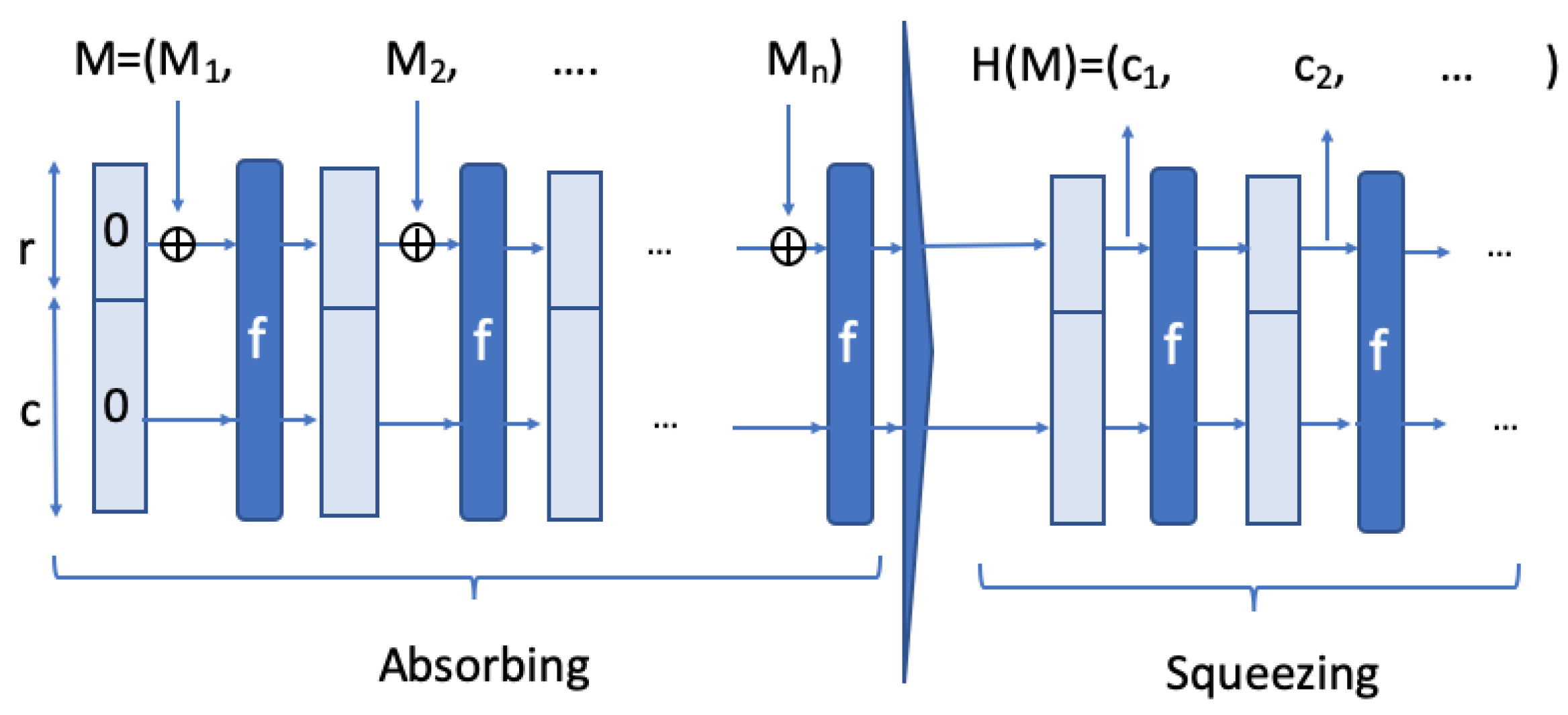
Sensors | Free Full-Text | Highly Efficient Symmetric Key Based Authentication and Key Agreement Protocol Using Keccak