Playing With KMS Key Policies. In this post,we'll play with some KMS… | by Vinayak Pandey | AVM Consulting Blog | Medium

Control Access to Your Data with Slack Enterprise Key Management and AWS KMS | AWS Partner Network (APN) Blog

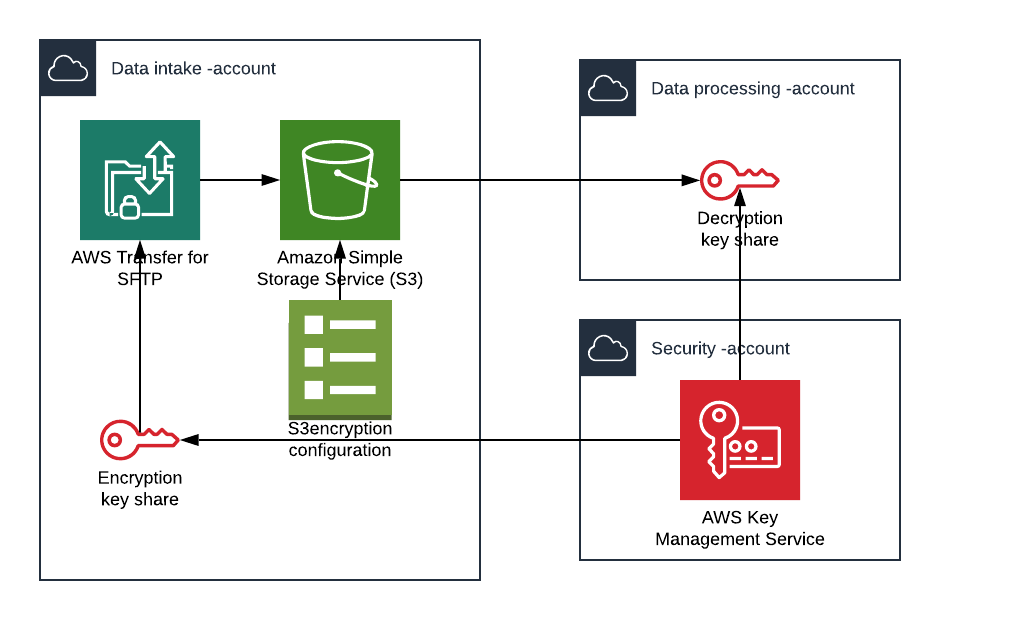
How to use KMS and IAM to enable independent security controls for encrypted data in S3 | AWS Security Blog



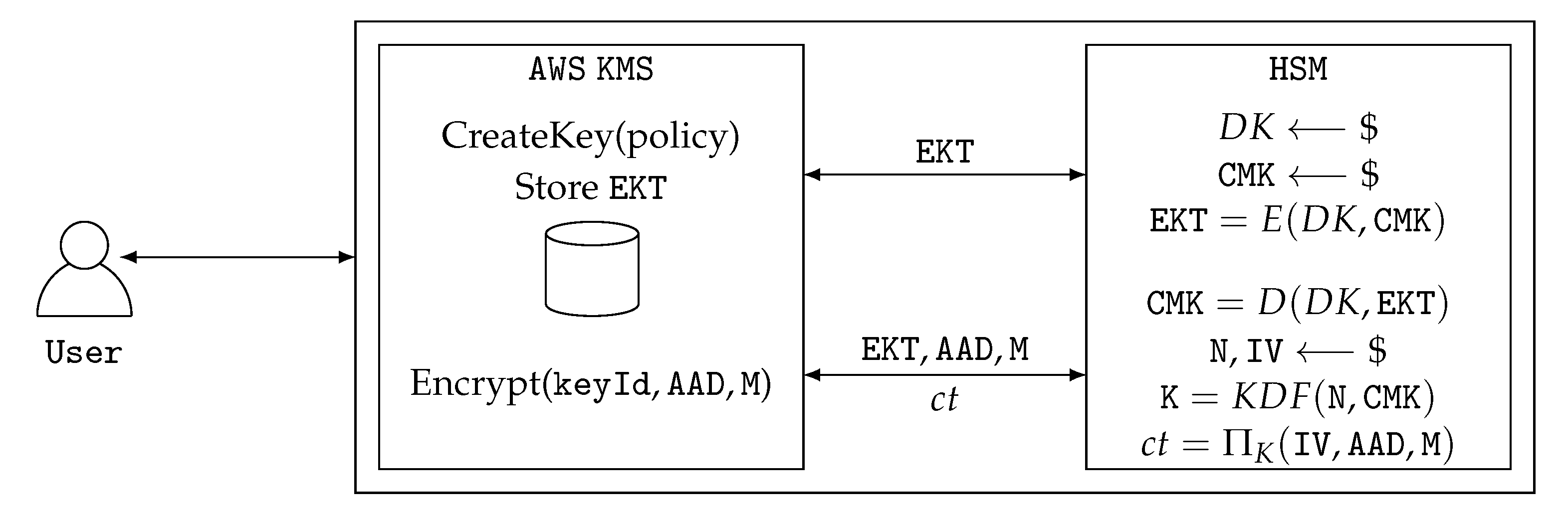


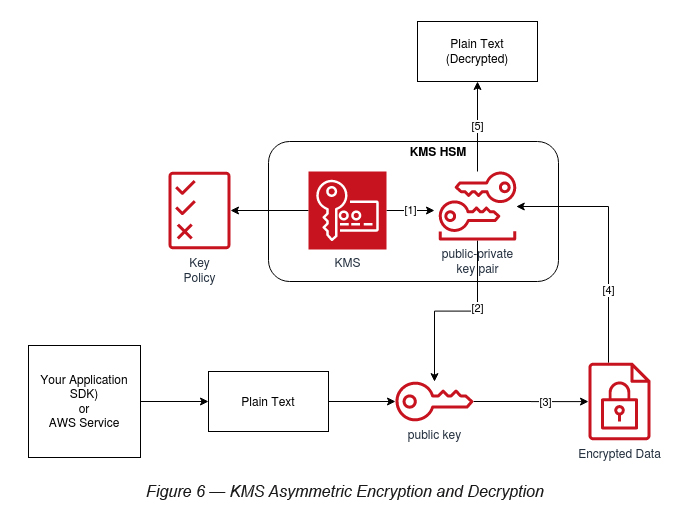








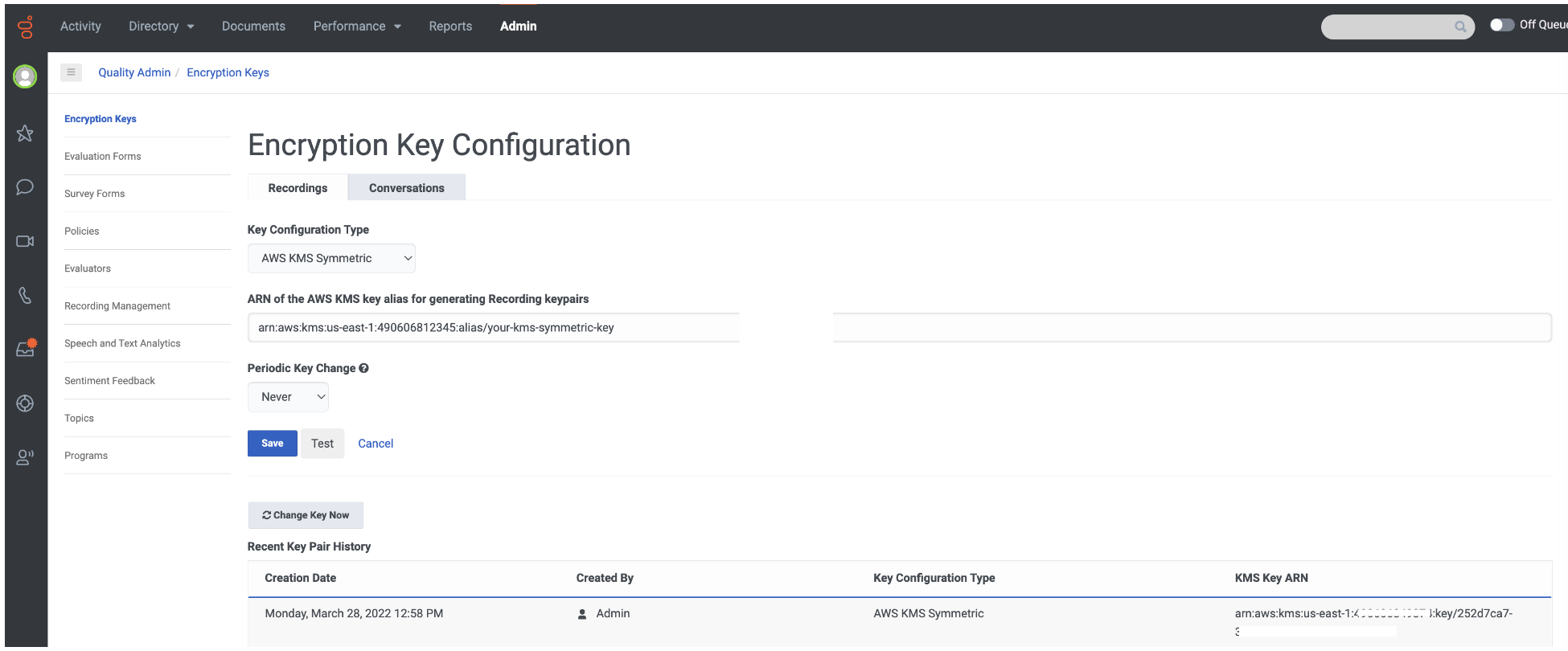
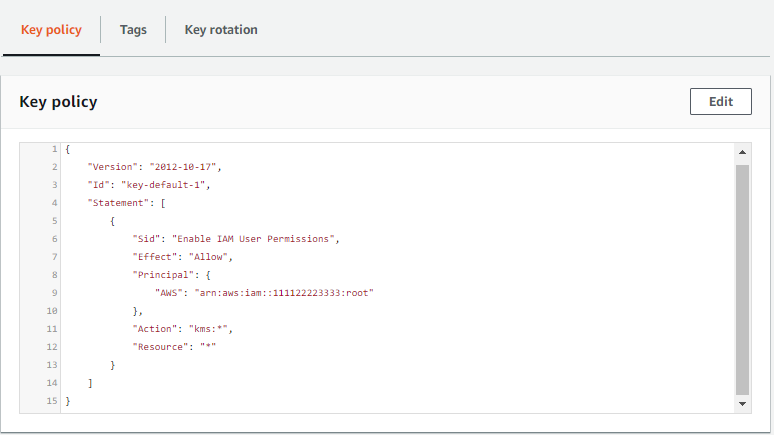


![Creating KMS keys - Learning AWS - Second Edition [Book] Creating KMS keys - Learning AWS - Second Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781787281066/files/assets/b6c74309-33f8-4cf5-8e14-970237d6c788.png)