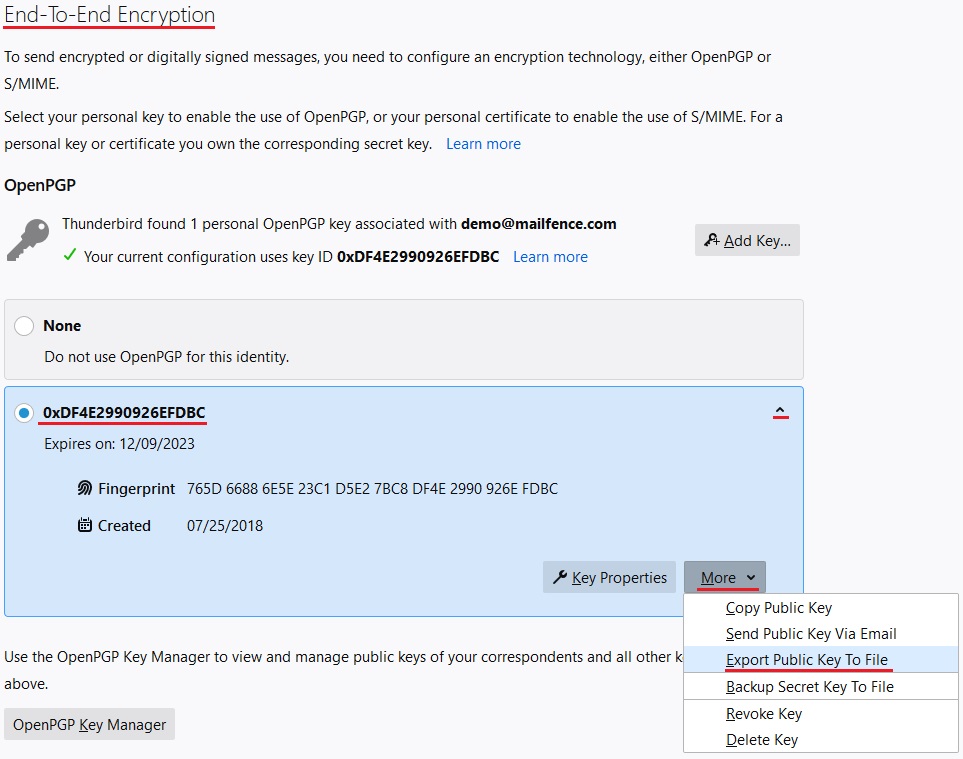
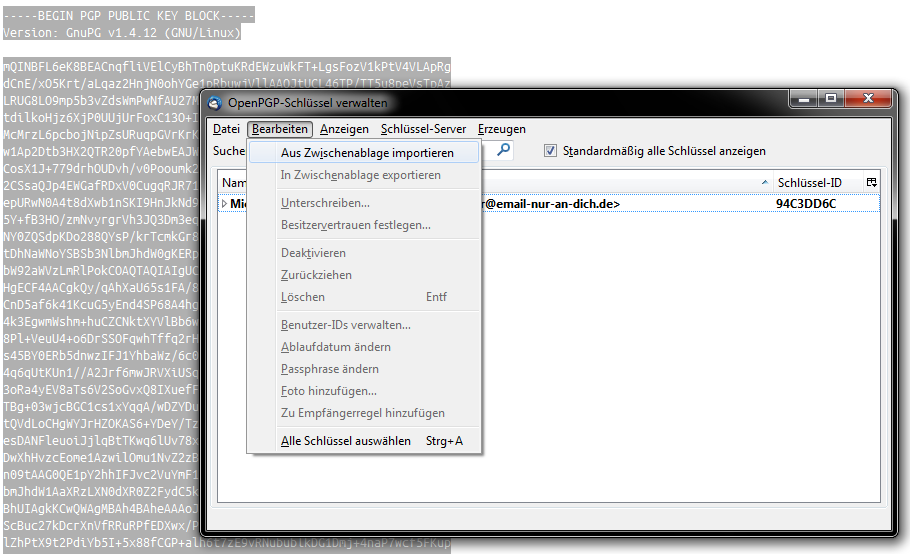
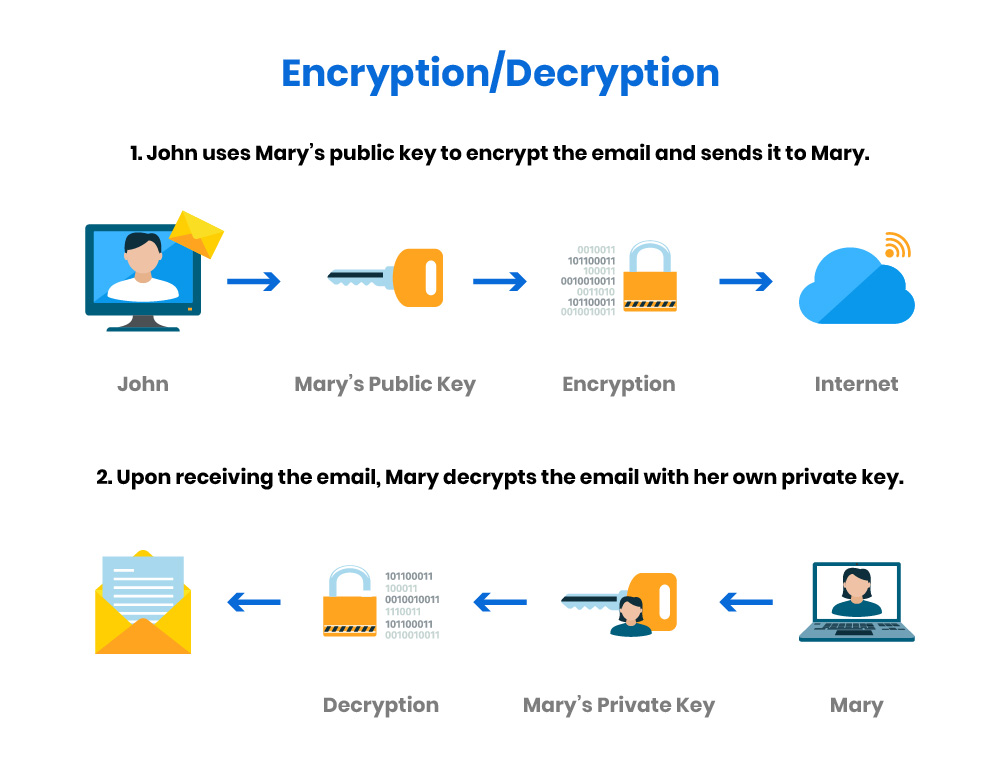
Email Encryption with PGP | How do I | Security Guidance | Security | Information Services | DePaul University, Chicago

Email Encryption with PGP | How do I | Security Guidance | Security | Information Services | DePaul University, Chicago
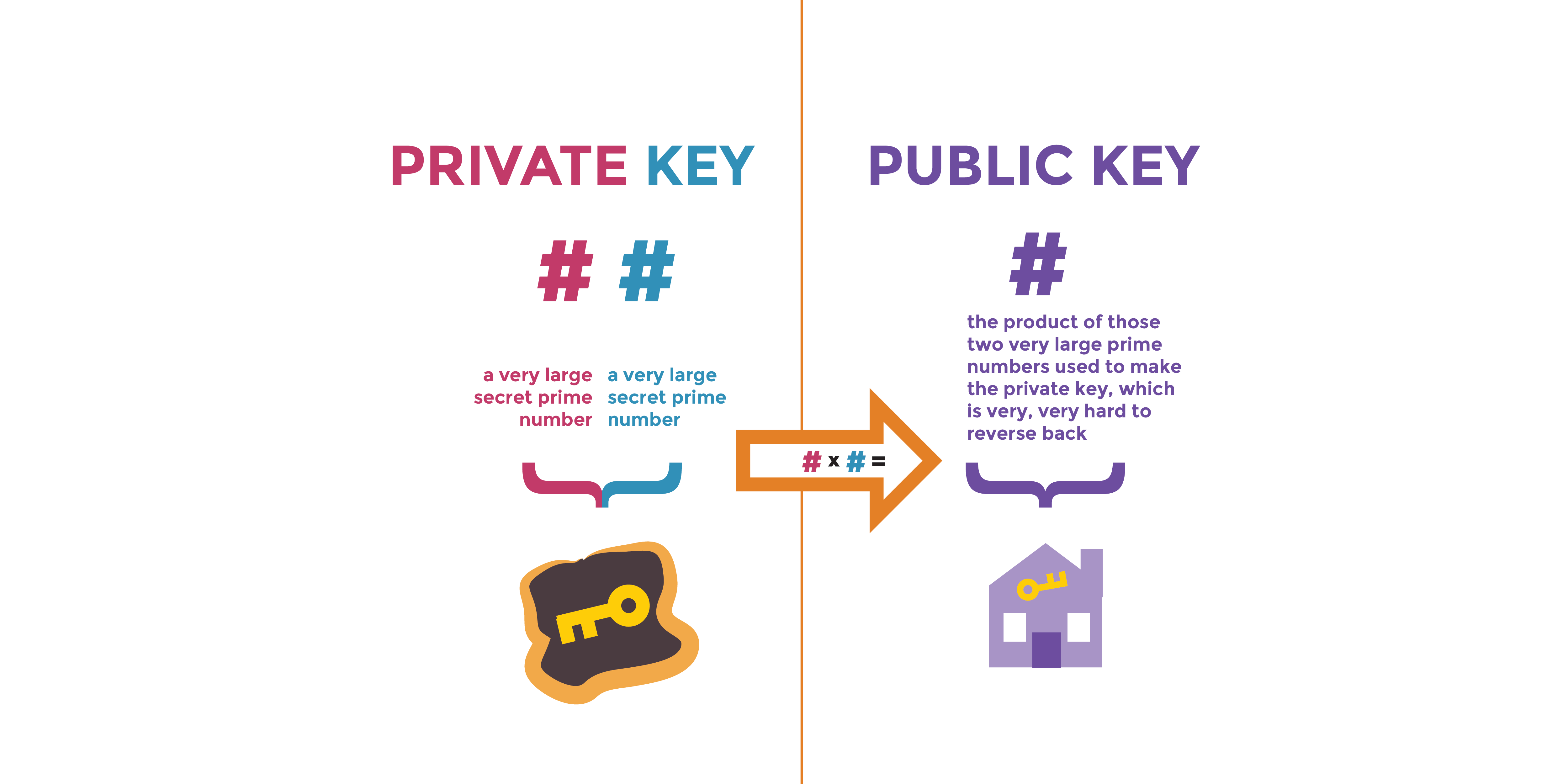
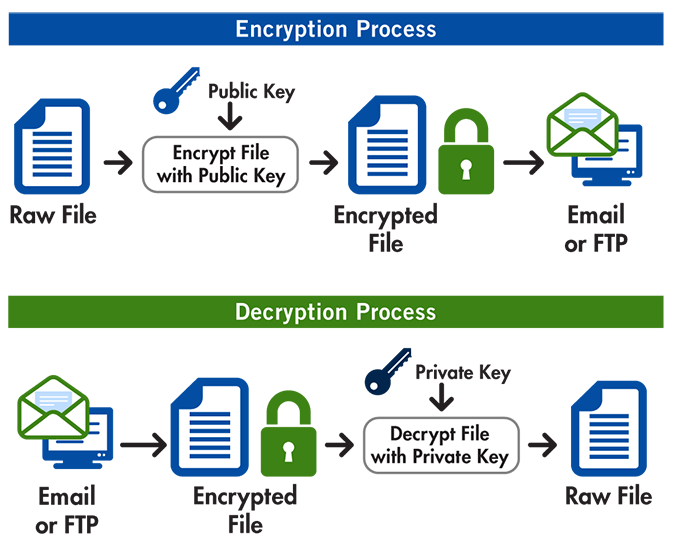
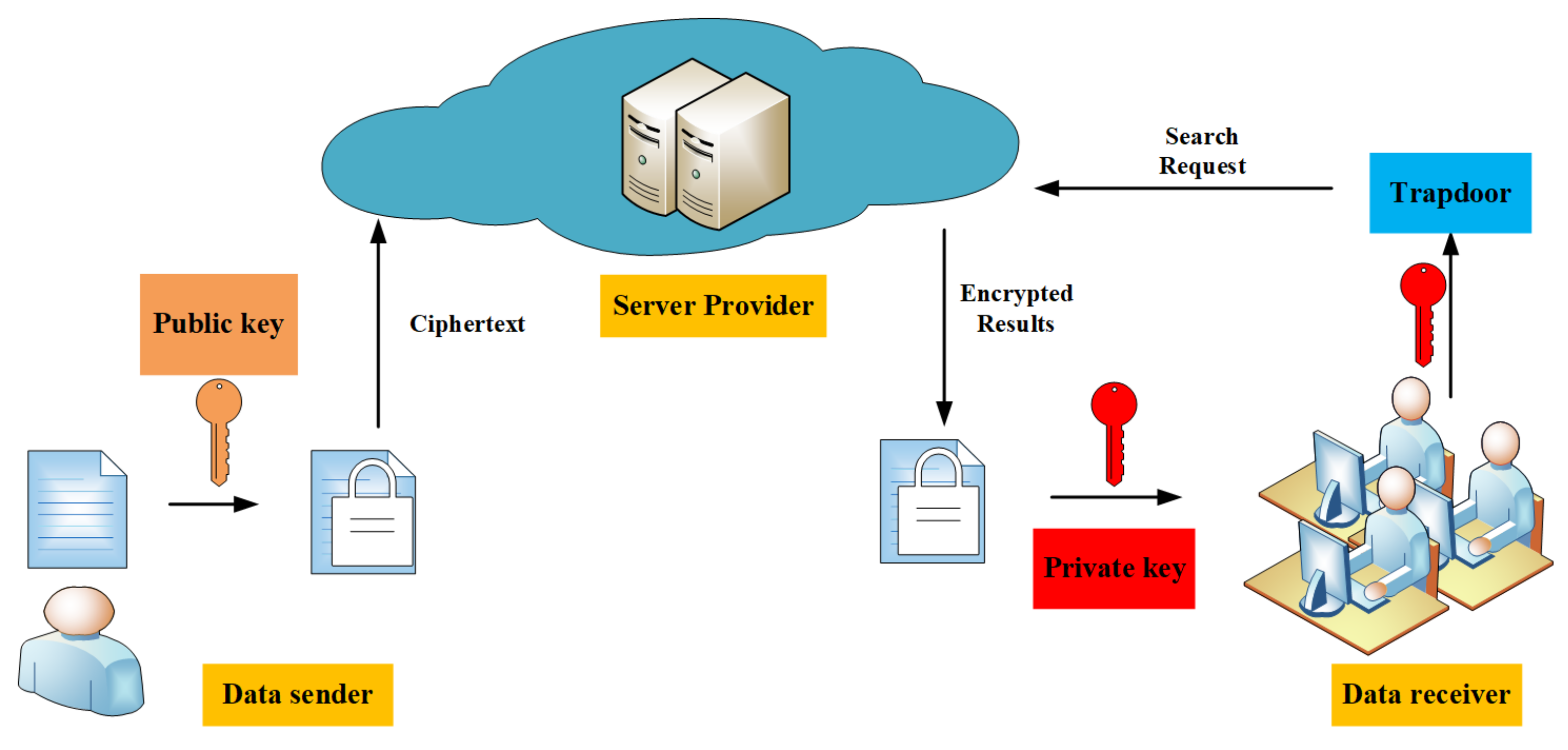
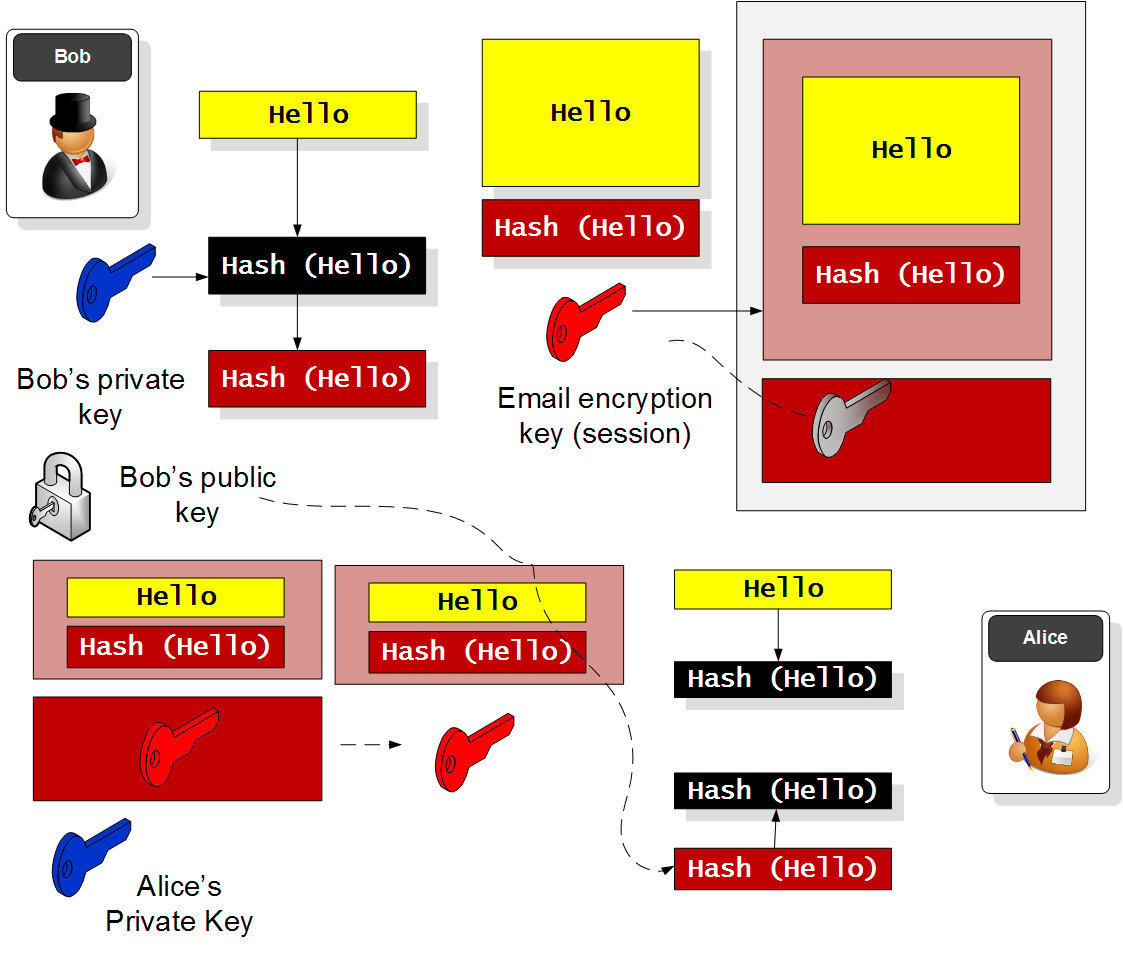
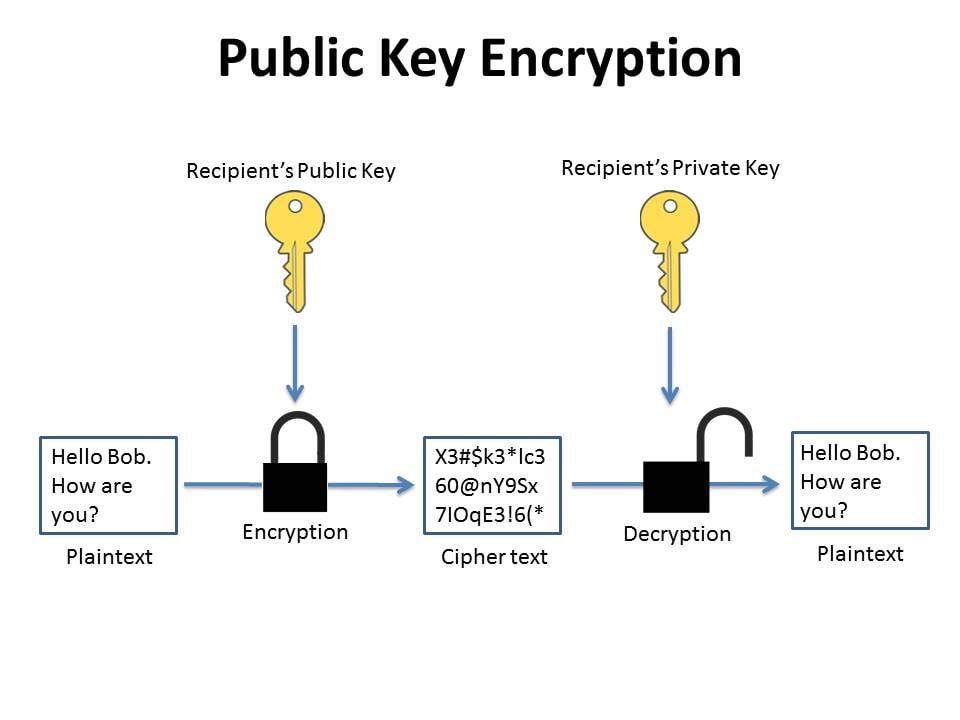
Bob send an email to Alice by encrypting the email using Alice's public... | Download Scientific Diagram